- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- REST + Access Import Job Failing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
REST + Access Import Job Failing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/17/2024
07:36 AM
- last edited on
03/17/2024
11:11 PM
by
![]() Sunil
Sunil
Hi,
I'm working on a REST integration and have the following Import Account JSON.
Previously I was able to run both account and access imports successfully. However, during the account import, I wasn't able to map the corresponding entitlements to the accounts and hence I had to change the account params as in the below JSON. (I added acctEntMappings within accountParams and then also added "processingType": "acctToEntMapping" under acctEntParams.
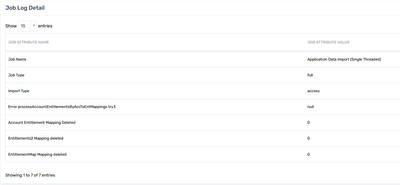
As soon as I did this, I'm able to see the account's customproperty31 getting populated as follows, however, the Access Import job has started failing (logs are attached) with some NULL pointer exception. Can you please help me with what could be the root cause?
User API response giving roles (which are mapped as entitlements in Saviynt).
|
"content": [
{
"mail": "test@abc.com",
"firstName": "Test",
"lastName": "1",
"displayName": "Test 1",
"businessPhone": null,
"homePhone": null,
"mobilePhone": null,
"roles": [
"b-user",
"b-admin"
],
"organizations": [
"98576ade-6990"
],
"primaryOrganization": "98576ade-6990",
"roleTenantFilter": "E_USER:bbqd_avd;E_ADMIN:bbqd_avp",
"passwordExpirationTimestamp": 1647061319658,
"passwordModificationTimestamp": 1639296463694,
"createdAt": "2021-12-12T08:02:39Z",
"lastModified": "2022-05-18T06:36:36Z",
"lastLoginDate": null,
"userState": "ENABLED",
"activationCodeCreationTimestamp": null,
"externalNames": {},
"sfUserId": null,
"verifiers": [],
"deleteTimestamp": null,
"preferredLocale": null,
"roleTenantFilterMap": {
"E_USER": [
"bbqd_avd"
],
"E_ADMIN": [ "bbqd_avp", ] },
"linkedToIdentity": false,
"id": "e26f6180-bbf7-46eb",
"links": [
{
"rel": "self",
}
]
},
|
CustomProperty31
| {"Role":{"entIds":["b-admin","b-user"],"keyField":"entitlementID"}} |
IMPORT JSON
| { "accountParams": { "connection": "acctAuth", "processingType": "SequentialAndIterative", "call": { "call1": { "callOrder": 0, "stageNumber": 0, "http": { "url": "https://BASE_URL/v1/users?size=2", "httpHeaders": { "Authorization": "${access_token}" }, "httpContentType": "application/x-www-form-urlencoded", "httpMethod": "GET" }, "listField": "content", "keyField": "accountID", "statusConfig": { "active": "ENABLED", "inactive": "DELETED" }, "colsToPropsMap": { "accountID": "id~#~char", "name": "mail~#~char", "customproperty1": "mail~#~char", "DISPLAYNAME": "displayName~#~char", "customproperty2": "firstName~#~char", "customproperty3": "lastName~#~char", "customproperty4": "company~#~char", "customproperty5": "primaryOrganization~#~char", "customproperty6": "roleTenantFilter~#~char", "customproperty7": "linkedToIdentity~#~bool", "customproperty11": "userState~#~char", "customproperty31": "STORE#ACC#ENT#MAPPINGINFO~#~char" } } }, "acctEntMappings": { "Role": { "listPath": "roles", "idPath": "", "keyField": "entitlementID" } } }, "entitlementParams": { "connection": "acctAuth", "processingType": "SequentialAndIterative", "entTypes": { "role": { "entTypeOrder": 0, "call": { "call1": { "callOrder": 0, "stageNumber": 0, "http": { "url": "https://BASE_URL/v1/roles", "httpHeaders": { "content-Type": "application/json", "Accept": "application/json", "Authorization": "${access_token}" }, "httpContentType": "application/json", "httpMethod": "GET" }, "listField": "content", "keyField": "entitlementID", "colsToPropsMap": { "entitlementID": "id~#~char", "entitlement_value": "roleEnumName~#~char", "customproperty3": "privileged~#~char", "customproperty4": "scope~#~char", "displayname": "description~#~char" } } } } } }, "acctEntParams": { "processingType": "acctToEntMapping" } } |
ERROR in the JOB:
[This message has been edited by moderator to disable URL hyperlink]
- Labels:
-
APIs
-
Authentication
-
Connectors
-
Imports
-
Provisioning
-
REST
-
Roles
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/18/2024 02:27 AM
Hello @nikhil,
Can you please try with the below sample,
{
"accountParams": {
"connection": "acctAuth",
"processingType": "SequentialAndIterative",
"call": {
"call1": {
"callOrder": 0,
"stageNumber": 0,
"http": {
"url": "https://BASE_URL/v1/users?size=2",
"httpHeaders": {
"Authorization": "${access_token}"
},
"httpContentType": "application/x-www-form-urlencoded",
"httpMethod": "GET"
},
"listField": "content",
"keyField": "accountID",
"statusConfig": {
"active": "ENABLED",
"inactive": "DELETED"
},
"colsToPropsMap": {
"accountID": "id~#~char",
"name": "mail~#~char",
"customproperty1": "mail~#~char",
"DISPLAYNAME": "displayName~#~char",
"customproperty2": "firstName~#~char",
"customproperty3": "lastName~#~char",
"customproperty4": "company~#~char",
"customproperty5": "primaryOrganization~#~char",
"customproperty6": "roleTenantFilter~#~char",
"customproperty7": "linkedToIdentity~#~bool",
"customproperty11": "userState~#~char",
"customproperty31": "STORE#ACC#ENT#MAPPINGINFO~#~char"
}
}
},
"acctEntMappings": {
"Role": {
"listPath": "content[0].roles",
"idPath": "id",
"keyField": "entitlementID"
}
}
},
"entitlementParams": {
"connection": "acctAuth",
"processingType": "SequentialAndIterative",
"entTypes": {
"role": {
"entTypeOrder": 0,
"call": {
"call1": {
"callOrder": 0,
"stageNumber": 0,
"http": {
"url": "https://BASE_URL/v1/roles",
"httpHeaders": {
"content-Type": "application/json",
"Accept": "application/json",
"Authorization": "${access_token}"
},
"httpContentType": "application/json",
"httpMethod": "GET"
},
"listField": "content",
"keyField": "entitlementID",
"colsToPropsMap": {
"entitlementID": "id~#~char",
"entitlement_value": "roleEnumName~#~char",
"customproperty3": "privileged~#~char",
"customproperty4": "scope~#~char",
"displayname": "description~#~char"
}
}
}
}
}
},
"acctEntParams": {
"processingType": "acctToEntMapping"
}
}
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/18/2024 03:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/18/2024 05:00 AM
Another thing I noticed Sudesh when I updated the JSON was that CustomProperty31 stopped populating the accesses for the users.
Since there is NO "id" (idPath) for the Role in the Account Import response, hence, it is unable to find accesses to be linked to users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/18/2024 07:52 AM
Hi @nikhil
There is no issue with your JSON, but the only thing that needs to be checked is if b-user and b-admin are mapped to entitlement ID in the entitlementParams because entitlementID is mentioned as the keyfield.
Please check this out.
Vedanth B.K
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/18/2024 10:16 AM
Thanks @Vedanth-BK It is already mapped correctly. I'm able to store the Entitlements (in the endpoint) and also Account-Entitlements within CustomProperty31. The only problem is that the job is failing even after reconciling everything as required.
Also, a question. Storing the values in CustomProperty31, is it the right approach, given I do not have a membership API and have to only leverage the user API?
Reason I ask is, if I try to assign user a role which is already present in CustomProperty31, Saviynt doesn't mark the task to "No Action Required". It tries to provision the same Entitlement even though it is present in CP31. This shouldn't happen ideally (similar to when the entitlements show up in Entitlements Hierarchy for a user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/18/2024 08:17 PM
What is CP31 of any sample account
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/18/2024 10:24 PM
Hi @rushikeshvartak I already provided that above.
Sample CP31 value:
| {"Role":{"entIds":["b-admin","b-user"],"keyField":"entitlementID"}} |
I'm just thinking whether populating this value is even helping anyhow. If Saviynt doesn't refer to this while processing a task, then is it even required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/18/2024 10:35 PM
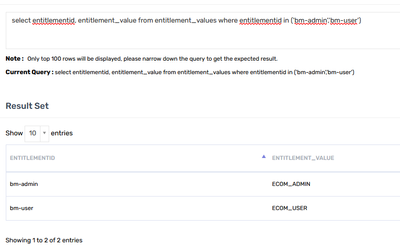
Also share
select entitlementid,entitlement_value from entitlement_values where entitlement_value in ('b-admin','b-user')
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/19/2024 04:25 AM - edited 03/19/2024 04:26 AM
Entitlement ID is bm-user / bm-admin. Entitlement ID serves as the key and has "ID" mapped to it. Entitlement Value is mapped to RoleEnum and hence is different.
I had modified the name from bm-admin / bm-user -> b-admin / b-user for security purposes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
03/19/2024 12:48 AM
Yes, if you get the mapping information as part of account's API then mapping cp31 is mandatory.
Could you please share a screenshot of the entitlementIDs for these ents- b-user and b-admin.
Vedanth B.K
- Saviynt-CyberArk Rest Integration Error in Identity Governance & Administration
- Application Connector Invalid access token provided in Identity Governance & Administration
- Technical rule not triggering in Identity Governance & Administration
- Remove Birthright Access if condition fails || Revoke Access task not created in Identity Governance & Administration
- Issue with Logical AD application Import in Identity Governance & Administration