- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- GitHub User Access Review - Permission Level
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
GitHub User Access Review - Permission Level
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
09/29/2023 12:47 AM
Hi All,
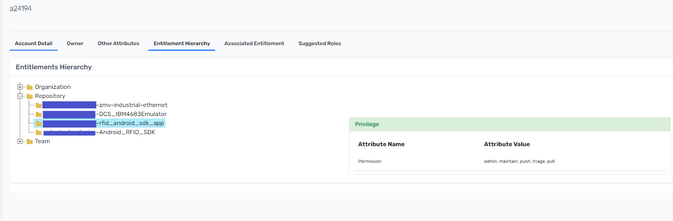
We followed the Saviynt GitHub Connector Guide and were able to import all the Repositories. For each Repository the permissions each repository collaborator has, is also imported (Though I do not know how and where the permissions are being stored).
In the entitlement hierarchy of a user account, when I click on the repository, I get a popup with the privileges the user has for that particular repository.
- Now when I launch a campaign for user access review, I see that there is an option to take action (tick, cross) for the repository, and there is a small hamburger menu clicking on which we get a popup with the privileges the user has for that repository.
Now, the client requirement is that they want to be able to take action at the permission level. i.e If a user has let's say admin privilege for a repository and that user should not have the admin privilege, they want to be able to only remove the admin privilege and not the complete repository access.
Presently, there is only the option to take action at the repository level in Saviynt. So, if the reviewer clicks on Reject the complete repository access will get revoked. But we don't want that...we want to be able to take action at the repository permission level.
How do we even achieve this? Or is it even achievable in Saviynt? If not, what can be the alternative?
Please advise.
Thanks,
Atul Singh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/03/2023 03:55 PM
Hi @AS5278 ,
Are the privileges defined for each entitlement ( in your screenshot above), attached as an associated entitlement to a respective entitlement?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/03/2023 11:18 PM
@DaanishJawed The privileges are not associated as child entitlement to the Repository type entitlements. The privileges are just appearing in a popup when clicking on the Repository name under entitlement hierarchy.
I have used the GitHub Connector for implementing the GitHub integration with Saviynt. I just used the sample JSON provided in Saviynt GitHub Connector documentation with some modifications. I do not completely understand how the privileges part has been implemented in the GitHub Connector.
I have used the ImportAcccountEntJSON from below link:
https://docs.saviyntcloud.com/bundle/GitHubRest-v23x/page/Content/Creating-an-Integration.htm
We have used the Import JSON from first part(GitHub Enterprise Cloud version).
If I have to make the privileges as child entitlement of the repository entitlement type, I understand that it might work in User Access Review. But how do I implement this?. The Import JSON is complex and I I am not able to construct the JSON.
Thanks,
Atul Singh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/04/2023 01:51 AM
@DaanishJawed @rushikeshvartak
If we want to import child entitlements in REST Connector, how can we implement it?. I am unable to find any sample JSON in Saviynt docs.
I found a similar post in forums but the solution link is no longer working.
https://forums.saviynt.com/t5/identity-governance/rest-importing-child-entitlements/m-p/15766#M6351
Please guide.
Thanks,
Atul Singh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/04/2023 12:30 PM
Hi @AS5278 ,
Can you check the below documents and see if this helps?
DOC Link - https://docs.saviyntcloud.com/bundle/REST-v23x/page/Content/Developers-Handbook.htm
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/05/2023 08:38 AM
@DaanishJawed Thank you for the above links, I went through the links but I could not understand how to import the child entitlements in our case.
We have an entitlementType called "Repository". Now for each repository there are a fixed set of permissions "admin,push,pull,triage,maintain". We want to import these permissions as the child entitlement of the repository type entitlement.
From the above links I could see a parameter "entMappingParams" which can be used for creating child entitlements. However, in the below configuration it is expecting that the child entitlements be coming in a "list".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/05/2023 09:54 AM
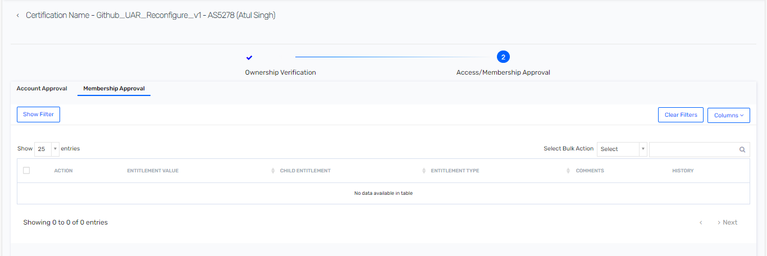
Also, how would this work even if we are able to somehow import the Repository permissions as child entitlements for each Repository.
In the "Membership Approval" there is no Account column. So how would this work?. The requirement is to remove a specific permission for a specific Repository for a specific User Account.
For example:
- Let's say user AS5278 is having access to a repository: "emc-road-media" and for this repository the permissions he is having are: "admin,maintain,triage,push,pull".
- But the reviewer decides that this user is not supposed to have the "admin" permission.
- Reviewer wants to remove only this 'admin' permission for that user for that particular repository. He does not want to remove the complete repository access for the user.
Is this possible to achieve in Saviynt?.
Thanks,
Atul Singh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/17/2023 01:31 AM
@DaanishJawed Any updates on this?. As I mentioned that we want to remove specific permissions for a repository for a specific user account through User Access Review.
So, if I import repository permissions(push,pull,triage,admin,maintain) as child entitlements of the repository(entitlement), how would this enable us to fulfill our requirement in UAR?.
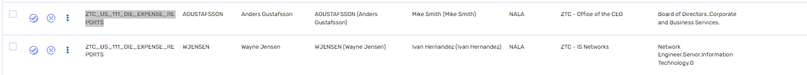
We have one such application, where we have child entitlements:
For example:
'ZTC_US_111_OIE_EXPENSE_REPORTS', is the entitlement and it has one child entitlement.
Now, if I go to the campaign I see 2 tabs: Account Approval and Membership Approval.
Under Account Approval, I get the option to approve or reject the entitlement access for the associated user accounts. I get no option to take action on the child entitlement of that entitlement.
Now, coming to the tab Membership Approval, here I get the option to approve or reject the entitlement and child entitlement association.
There is no account column here. So, if I want to remove the child entitlement for an entitlement for a specific User Account, how do I do this?.
Please advise if this can be done in Saviynt in any way. We are stuck with this since weeks and unable to proceed further.
Thanks,
Atul Singh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/17/2023 01:35 PM - edited 10/17/2023 01:48 PM
Hi @AS5278 ,
Editing my Response.
I was checking this internally along with performing some test cases. So child entitlements currently can only be part of EO campaign. But it will be displayed as you are seeing along with the parent entitlement. Hence, you will have to take action on both Parent and Child entitlement which does not satisfy your use-case.
Can you try setting an owner as a primary certifier for the child entitlement too? So this way the child entitlement will come in as a separate entitlement.
For Example -
Entitlement A - Parent entitlement
Entitlement B - Child entitlement
Currently it is displayed as below
Entitlement A ----- > Entitlement B
Now if you add a primary certifier for the child entitlement too then it will be displayed as -
Entitlement A ----- > Entitlement B
Entitlement B
Please try this option. If this does not work too then this is currently not supported and will be an enhancement.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/20/2023 03:24 AM
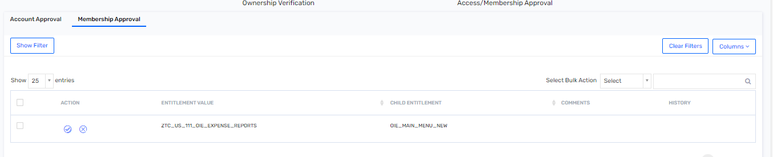
If I get two rows:
Entitlement A (Parent) --> Entitlement B(Child)
Entitlement B(Child)
If I click on reject for Entitlement B(Child), how will it work actually? How will this child entitlement get revoked for only that particular parent (Entitlement A) and for that particular User.
Also, in the 'membership approval' tab there is no Account column.
Let me try to explain our use case:
We have multiple Repositories which we have imported as entitlements in Saviynt. Now, each repository is having a fixed set of permissions (5 permissions). Every user who has access to any Repository can have a subset of these 5 permissions.
So, let's say there is a User X who has access to repository R and has three permissions for that particular repository (admin, push, pull).
Now, the reviewer wants to review the permissions the user has for each repository. They want to be able to remove the unnecessary permissions that user has for that Repo.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/24/2023 02:23 PM
Hi @AS5278 ,
We have already understood your use-case from previous comments.
Account column will not be visible under the membership approval section. This is expected. Accounts will only be displayed under Account Approval section.
The approach suggested by me above will only remove the child entitlement from the parent entitlement which does not match your use-case.
So this use-case is not currently supported. Please have this posted in the Ideas portal - https://ideas.saviynt.com/ideas/
Thanks.
- Campaign data in Saviynt for review in Identity Governance & Administration
- Three tiers certifier in Identity Governance & Administration
- 24.4 Version Upgrade - New field is added in Review Page while Provisioning HA - User Accounts in Identity Governance & Administration
- Service Account Campaign: Skip Ownership Verification Step in Service Account Access Review in Identity Governance & Administration
- User visibility and Data separation between multiple projects in Identity Governance & Administration