Click HERE to see how Saviynt Intelligence is transforming the industry.
|
Click HERE to see how Saviynt Intelligence is transforming the industry. |
05/31/2023 02:08 AM
In the same user update rule I'm trying to include the following Actions:
Enable Account and Change Password but these 2 actions are not being instant provisioned.
And I can see in the debugLog that the Change Password is always triggered first and resulting in error, probably because the account is not enabled at the moment:
DEBUG services.SaviyntCommonUtilityService - returnmap for changepassword = [errorList:[No account found for user : TESXAW], taskIdList:[]]
The Instant provisioning for ChangePassword and Enable Account are both working when only 1 action is included but when I have both chained, only the Enable Account works.
Is this a bug or am I missing some configuration or do I need to list ALL tasks under Task Execution Hierarchy?
I have configured the following:
On or Off: UI Wait for Instant Provisioning (not really sure why is this doing though)
Off or On: Enable multithreading for instant provisioning
Task Execution Hierarchy: Enable Account, Change Password
(And also configured Instant Provisioning for the endpoint)
06/02/2023 07:21 AM
Hi @Victor
Did you check the logs? Just check to see which task is being picked up first , as per your config in task exec hierarchy it should take up the enable account task and enable it, If you check the logs you would get a idea of what is happening, You can attach the snippet of logs where task is picking up otherwise.
Thanks
Darshan
06/06/2023 12:56 AM
Hi @Darshanjain
Yes, I can see in the debugLog that the Change Password is always triggered first and resulting in error, probably because the account is not enabled at the moment.
I have tried to configure the Task Execution Hierarchy as follows:
Task Execution Hierarchy: Enable Account, Change Password
But still the order was not followed. Is this configuration not correct and all tasks should be listed or is this actually broken and a FD ticket should be created?
06/06/2023 04:23 AM
Can you please attach a snippet in the logs where it mentions the task hierarchy order and picks up the change password task before enable account task.
Thanks
Darshan
06/13/2023 03:17 AM - edited 06/13/2023 03:46 AM
Sorry @Darshanjain, took some time as we had AD certificate issues, see below some logs and config details, I cannot see any mention to the hierarchy in the debuglog, after CP60 is changed.
Enable account and Change Password are triggered by the User Update Rule: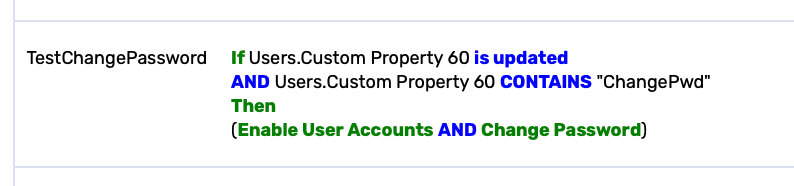
But I can see that No account found for the user
returnmap for changepassword = [errorList:[No account found for user : TESXAW], taskIdList:[]]
2023-06-13/09:51:32.681 [{}] [quartzScheduler_Worker-1] DEBUG rulerun.RuleRunService - START Rule Run for userkey=13864 , username=TESXAW , objectdata = [customproperty60:[ChangePwdC, ChangePwd10],] , userchangeMap = [customproperty60:[ChangePwdC, ChangePwd10],]
2023-06-13/09:51:33.118 [{}] [quartzScheduler_Worker-1] DEBUG saviynt.ImportExternalDbService - Final query to get accounts for enableUserAccounts::SELECT USER_ACCOUNTS.USERKEY,USER_ACCOUNTS.ACCOUNTKEY,ACCOUNTS.ENDPOINTKEY,ACCOUNTS.SYSTEMID FROM USER_ACCOUNTS,ACCOUNTS,USERS where USER_ACCOUNTS.ACCOUNTKEY=ACCOUNTS.ACCOUNTKEY AND USER_ACCOUNTS.USERKEY = USERS.USERKEY AND ( ACCOUNTS.ACCOUNTTYPE <> 'Service Account' OR ACCOUNTS.ACCOUNTTYPE is null )AND (ACCOUNTS.STATUS='Manually Suspended' OR ACCOUNTS.STATUS='2') AND ACCOUNTS.ENDPOINTKEY IN (SELECT ENDPOINTKEY FROM ENDPOINTS WHERE ENDPOINTKEY IN (5) AND STATUS=:status) AND USER_ACCOUNTS.USERKEY IN
2023-06-13/09:51:33.120 [{}] [quartzScheduler_Worker-1] DEBUG saviynt.ImportExternalDbService - List of User Account to be Enabled - [13864_631732]
2023-06-13/09:51:33.137 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - hanaRuleAttributeQuery select h.attributeConfig,h.objectvalue from HanaRuleAttribute h where h.hanaRule=:hanaRuleKey and h.conditionoraction='ACTN'
and h.objectname=:enableUserAccountType and h.attributeConfig is not null and (find_in_set(5,h.objectvalue) or h.objectvalue=0 )
2023-06-13/09:51:33.139 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - HanaRule attributeConfigValue null
2023-06-13/09:51:33.139 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - futureStartDateForTask in checkForFutureDateForTaskToBeCreatedViaUserUpdateRule() null
2023-06-13/09:51:33.139 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - ---------------------------------------------------------------------------------------------------------
2023-06-13/09:51:33.146 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - baseUrlForEmail value in externalConfig : [:]
2023-06-13/09:51:33.146 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - baseUrlForEmail is missing in the externalConfig file. Please add it !
2023-06-13/09:51:33.152 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - Config for ARSTASKCREATETEMPcom.saviynt.ecm.utility.domain.EcmConfig : ARSTASKCREATETEMP
2023-06-13/09:51:33.164 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskHelperService - taskemailtemplates = [{"emailTemplateType":"1","taskType":"3","emailTemplate":"New employee credential information"},{"emailTemplateType":"1","taskType":"5","emailTemplate":"Password Change"}]
2023-06-13/09:51:33.164 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskHelperService - emailTemplates for template type = 2 [:]
2023-06-13/09:51:33.174 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - users = TESXAW
2023-06-13/09:51:33.174 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - qry: SELECT AC.name, AC.accountkey, AC.ENDPOINTKEY FROM ACCOUNTS AC, USER_ACCOUNTS UA, ENDPOINTS EP, SECURITYSYSTEMS SS WHERE UA.USERKEY=13864
AND AC.ACCOUNTKEY=UA.ACCOUNTKEY AND EP.ENDPOINTKEY=AC.ENDPOINTKEY AND EP.SECURITYSYSTEMKEY = SS.SYSTEMKEY AND (AC.NAME NOT LIKE '%Deleted on%'
AND AC.STATUS NOT IN ('2','4','3','suspended from import service','manually suspended','inactive','decommission inactive','decommission active')) AND EP.ENDPOINTKEY IN (5)
AND (AC.ACCOUNTTYPE NOT LIKE 'Service Account' OR AC.ACCOUNTTYPE IS NULL)
2023-06-13/09:51:33.176 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - returnmap for changepassword = [errorList:[No account found for user : TESXAW], taskIdList:[]]
2023-06-13/09:51:33.181 [{}] [quartzScheduler_Worker-1] DEBUG changeaction.UserChangeActionHelperService - retrofitDisabled = false
2023-06-13/09:51:33.196 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - CONSIDER_ASSIGNEDFROMROLE_IN_BR_REMOVAL = 1
2023-06-13/09:51:33.196 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - considerassignedfromrole = true
2023-06-13/09:51:33.202 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - CONSIDER_ASSIGNEDFROMROLE_IN_BR_REMOVAL = 1
2023-06-13/09:51:33.202 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - considerassignedfromrole = true
2023-06-13/09:51:33.205 [{}] [https-jsse-nio-443-exec-167] DEBUG auth.LoginController - Default Setup
2023-06-13/09:51:33.205 [{}] [https-jsse-nio-443-exec-167] DEBUG auth.LoginController - URL TO SAML LOGIN2=/ECM/login/index?login=true&idp=https://sts.windows.net/48480d52-e8fe-4ec3-8b88-778d92953ce7/
later I see the Rule completed:
2023-06-13/09:51:36.282 [{}] [quartzScheduler_Worker-1] DEBUG rulerun.RuleRunService - START Rule Run for userkey=13864 , username=TESXAW , userchangeMap = [customproperty60:[ChangePwdC, ChangePwd10]] Completed
And only later I see the AD account being enabled:
2023-06-13/09:51:36.438 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - Validating tasks for Securitysystem - Active Directory
2023-06-13/09:51:36.440 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - includeinactiveusersandacc = true
2023-06-13/09:51:36.440 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - Key has Accounts
2023-06-13/09:51:36.443 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - accountName = TESXAW , taskType = 6 accountkey = 631732
2023-06-13/09:51:36.482 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - Entitlements already assigned to the account-TESXAW[631732] - [12481, 2146, 4935, 1928, 12488, 13032, 2057, 2185, 2345, 2387, 12885, 2362, 12477, 2463]
2023-06-13/09:51:36.482 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - Entitlement accEntMap = [12481:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 85411334], 2146:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474924], 4935:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474923], 1928:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474927], 12488:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474929], 13032:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 85426436], 2057:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474932], 2185:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474925], 2345:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474931], 2387:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474930], 12885:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 85411332], 2362:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474928], 12477:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 85411328], 2463:[com.saviynt.ecm.identitywarehouse.domain.Account_entitlements1 : 88474926]]
2023-06-13/09:51:36.482 [{}] [quartzScheduler_Worker-1] DEBUG services.SaviyntCommonUtilityService - ProvLimitJSONMap=[:]
2023-06-13/09:51:36.482 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - Task Type = 6 , total tasks = 1
2023-06-13/09:51:36.482 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - tasktypeStr = ENABLEACCOUNT , provLimitStr = 5000
2023-06-13/09:51:36.482 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - tasktypeStr = ENABLEACCOUNT , provlimit = 5000
2023-06-13/09:51:36.487 [{}] [quartzScheduler_Worker-1] DEBUG services.ArsTaskService - Calling AD enableAccount with Sec System - Active Directory and tasklist - [TESXAW:[com.saviynt.ecm.task.ArsTasks : 458842]]
Task Execution hierarchy including only Enable Account, Change Password
I guess the initial question remains: Is this a bug that should have an FD ticket created or is my configuration not correct or it is not possible to achieve instant provision to first enable the account and then change the password?
06/16/2023 05:03 AM
@Darshanjain I did open a FD ticket for this (#1638545) but the answer was:
" This has been reviewed by support team and it is implementation related.
As per the new process, such requests will be reviewed and addressed directly by respective product/engineering teams. "
Could you please verify with them what am I missing?
06/16/2023 05:47 AM
Please reopen and mention the forum link saying the same it was requested to open the ticket to check the issue
Thanks
Darshan
06/17/2023 11:30 AM
This is missing functionality , rule should have execute on feature to trigger which action to called first
08/17/2023 04:39 AM
@rushikeshvartak so you mean that this is not possible then?
08/21/2023 02:59 AM - edited 08/21/2023 02:59 AM
If I understand the issue correctly, it looks like the task itself is not getting created in which case the task execution hierarchy does not matter, as that is for processing the task and not for creation. Also, Change Password task is not created for Disabled User.
To execute such cases, you can use a Sav4Sav connection where you can fetch all the users for which Enabled Account task is Completed for the day and then update the user's profile with some value, which in turn can be used to trigger a Change Password task, which then should execute successfully.