- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- Re: SAML SSO Configuration question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/02/2023 02:20 AM
Hello,
We have setup our SAML SSO configuration for our customer instance (v23.1) using the documentation Here
We have done this before on our own instance and are now doing it for a customer. We have the same configuration on both sides, but for some reason this one will not redirect us to the IDP page once we enter https://<URL>/ECM . We are on different versions on both instances though, so this might be the issue.
The logs show that a IDP Metadata file cannot be found, but 2 logs later it says it's reading the IDP metadata file. Could this be an issue with the file directory?
We have setup our configuration in our AuthenticationConfig.Groovy like this:
Any help would be greatly appreciated.
Solved! Go to Solution.
- Labels:
-
Defect or Issue
-
Need Information
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/02/2023 03:17 AM
Hello @Robbe_Cronos,
Could you please confirm the following information for me?
1. Is the IDP metadata file path correct? If the file cannot be found, the process will fail on the first attempt.
2. Could you please verify the name of the IDP file in AuthenticationConfig.Groovy?
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/02/2023 06:12 AM - edited 05/02/2023 06:13 AM
Thank you for the response.
1. Where can we check if the file path for the IDP metadata file is correct? We used the path
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/02/2023 06:54 AM
We have fixed the issue. For some odd reason, the IDP metadata file and the SP metadata file don't need a path in front of them. For the Keystore file you do need a path in front of it? Don't know why it is configured like that but it works now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/02/2023 07:04 AM
HI Robbe_Cronos,
You don't have to specify the entire file path of the Metadata file you can only specify the name of the metadatafile and the file name must contain _idp or _sp files respectively. for example:
grails.plugin.springsecurity.saml.metadata.providers = [ping :'azidp_idp.xml']
grails.plugin.springsecurity.saml.metadata.sp.file = 'sp_sp.xml'
The metadata.defalultidp will be like
grails.plugin.springsecurity.saml.metadata.defaultIdp = '<Entityid persent in the idp metadatafile>'
The below SSO configurations will be enough for the SSO to be working as follows :
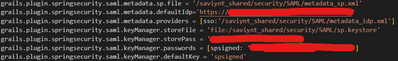
grails.plugin.springsecurity.saml.keyManager.storeFile = 'file:/saviynt_shared/security/SAML/<Keystorefilename>.jks'
grails.plugin.springsecurity.saml.keyManager.storePass = '<Password used in Keystore>'
grails.plugin.springsecurity.saml.keyManager.passwords = [ selfsigned: '<Keystore password>' ]
grails.plugin.springsecurity.saml.keyManager.defaultKey = 'selfsigned'
grails.plugin.springsecurity.saml.metadata.defaultIdp='<entityid of the idp metadata file>'
grails.plugin.springsecurity.saml.metadata.providers = [ping :'<idp metadata Filename>_idp.xml']
grails.plugin.springsecurity.saml.metadata.sp.file = '<Sp metadata filename>_sp.xml'
grails.plugin.springsecurity.saml.metadata.sp.defaults = [
local: true,
alias: '<Entityid used in the SP metadata file>',
securityProfile: 'metaiop',
signingKey: 'selfsigned',
encryptionKey: 'selfsigned',
tlsKey: 'selfsigned',
requireArtifactResolveSigned: false,
requireLogoutRequestSigned: false,
requireLogoutResponseSigned: false,
idpDiscoveryEnabled: true]
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
06/16/2023 07:21 AM
for Azure AD does this change in place of ping will it be AzureAD??
grails.plugin.springsecurity.saml.metadata.providers = [ping :'<idp metadata Filename>_idp.xml']
- Assign SAV Role as an Entitlement in Enterprise Role in Identity Governance & Administration
- SAP GRC mitigation control GRAC_API_MITIGATION_ASSIGMENT in Application Access Governance
- PROFILE MENU - Shows Reset Security Questions and Change User API Password Options in Identity Governance & Administration
- Activer SSO doesn't not work for EIC 23.11 in Identity Governance & Administration
- saml sign assertion in Identity Governance & Administration