Click HERE to see how Saviynt Intelligence is transforming the industry.
|
Click HERE to see how Saviynt Intelligence is transforming the industry. |
08/15/2023 05:06 PM
Hi,
We need to implement role based pam for Azure workloads like Azure console, windows, unix and database and On-premise workloads like windows, unix and database . The documentation only has a process flow diagram on at https://docs.saviyntcloud.com/bundle/CPAM-Admin-Guide-v23x/page/Content/B-Key-Concepts/PAM-Methods.h....
But we were unable to find any more details than that i.e., end to end steps or an example for an administrator to set it up or for an end user to use to request privileged access.
There are other information which we could find in bits and peace's but nothing which we can join together to make sense.
Feature matrix for Windows, Unix and database says - Role-based access elevation --Emergency (Role) elevation/Access capability.
Is Role based privileged access managed and requested as Emergency roles as described at https://docs.saviyntcloud.com/bundle/EIC-User-v23x/page/Content/03-mang-accs/ars-mang-emrg-accs.htm ?
But privileged access to on-premise at https://docs.saviyntcloud.com/bundle/CPAM-User-Guide-v23x/page/Content/A-PAM-Requests/Privileged-Acc... does not talk about it or give an example to tie them together as a process to request role base privileged access to windows, unix or database.
Privileged access to applications like AWS does talk about Role based access at https://docs.saviyntcloud.com/bundle/CPAM-User-Guide-v23x/page/Content/A-PAM-Requests/Privileged-Acc...
>>
Log in to EIC.
Click Applications > Home.
Click Menu > Privileged Access > New Privileged Access, and then click the required application.
The Application Console page with the list of applications/systems is displayed.
Go to a specific application and click Select Role to choose the appropriate role.
<<<<
We are not able to link anything together to understand end to end process.
Questions:
1. How emergency role is different from Role based PAM?
2. What are the end to end steps to configure Role based PAM for below workloads
3. What is end to end step for an end user to request role based privileged access for each workload mentioned above?
4. What is the end to end step for an end user to access the privileged session for each workload mentioned above?
Thanks,
Vivek
Solved! Go to Solution.
08/17/2023 01:19 AM
Please find the answers:
Questions:
1. How emergency role is different from Role based PAM?
Role-based PAM is a feature within the CPAM module and this feature is addressed by setting the role type as an emergency role type with the required entitlements added to the role so that the PAM users can request the role.
2. What are the end to end steps to configure Role based PAM for below workloads
Please refer to this document:
3. What is end to end step for an end user to request role based privileged access for each workload mentioned above?
Please refer to this document:
4. What is the end to end step for an end user to access the privileged session for each workload mentioned above?
Please refer to this document:
08/17/2023 05:37 PM
Hi,
The documentation shared does not include any details on requesting Role based privileged access for any of the Windows, Linux or Database workloads.
Example: There is an emergency role which provides admin access to user i.e adds user to Administrator group on Active Directory. After requesting and approval for this role:
1. How would the user access a Windows workload?
2. How we can monitor the user session in this case?
3. How an authorised person can terminate the session while monitoring?
There are clear steps with examples available in documentation for credential and credential less access of shared accounts? Where we can find examples or steps for Role based PAM?
Regards,
Vivek
08/17/2023 11:47 PM
Hi @vivekbksingh
Please find the answers below.
1. How would the user access a Windows workload?
Please refer to the below documentation.
https://docs.saviyntcloud.com/bundle/CPAM-User-Guide-v23x/page/Content/A-PAM-Requests/Privileged-Acc...
2. How can we monitor the user session in this case?
Please refer to the below documentation.
https://docs.saviyntcloud.com/bundle/CPAM-Admin-Guide-v23x/page/Content/F-Manage-PAM-Session/Monitor...
3. How an authorised person can terminate the session while monitoring?
Please refer to the below documentation.
https://docs.saviyntcloud.com/bundle/CPAM-Admin-Guide-v23x/page/Content/F-Manage-PAM-Session/Monitor...
Regards,
Vikas J V
If this reply answers your question, please click the Accept As Solution button to help future users with similar problems.
08/18/2023 02:10 AM
Hi Vikas,
I am already aware and read the document links shared above. But any of these does not give a clear picture of requesting role based pam. Let me try again
Lets say my request for emergency role is approved and my Active Directory domain account has now admin privileges as part of emergency role.
If i go and try to access a windows machine via privileged access option in EIC does, do we get any option to launch my session on windows machine as my logged in user?
The document says instructions will be provided. I just wanted to see or know how these instructions will look like
Role-based | For role-based access, the instructions and link to access the endpoint are provided to the user. |
Regards,
Vivek
08/28/2023 04:51 PM
Any update on this?
09/03/2023 10:30 PM
Hi @vivekbksingh ,
We are checking this internally and update you on the same.
Regards,
Vikas J V
10/12/2023 01:50 AM
Hi Vikas,
Were you able to check this internally.
Regards,
Vivek
10/12/2023 05:26 PM
@vivekbksingh Thank you for being so patient and waiting long for the answer. I will explain the process below.
Scenario 1 : For target systems like AWS, GCP, Azure AD (Entra Directory), Salesforce, etc. where roles are created and managed
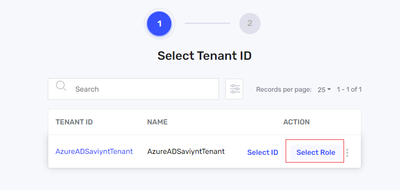
Scenario 2 : For target systems like Active Directory where Groups are available
Scenario 3 : For Unix, Windows and DB Workloads
@vivekbksingh Thank you for being so patient and waiting long for the answer. I will explain the process below.
Scenario 1 : For target systems like AWS, GCP, Azure AD (Entra Directory), Salesforce, etc. where roles are created and managed

Scenario 2 : For target systems like Active Directory where Groups are available
Scenario 3 : For Unix, Windows and DB Workloads
Now, the important point to note here is that Requesting these roles will result in adding the underlying entitlement to the logged in user's personal account on the target. If you are looking to launch privilege session to the target post gaining access to the Emergency Access role, the user's personal account should be onboarded for PAM.
Finally, in the AD scenario you asked for, this is what would happen:
I hope this clarifies. Please let me know in case of any further questions.
Thanks
Nagesh K
10/12/2023 05:35 PM
Hi Nagesh,
Thanks for the detailed explanation. For scenario 3, I agree role based access is not required.
Regards,
Vivek