Use Case
Integrate Tenable application with EIC to facilitate the access certification , provisioning and de-provisioning of Tenable roles access to organization users. Tenable exposes REST APIs for CRUD operations on tenable accounts/access objects.
Pre-requisites
1. Register in the Tenable platform and then get a user created for API usage with username password. This username password will be used to fetch the access token/x-api-key/x-securityCenter key.
2. Verify that generated token/key is able invoke the underline Tenable REST APIs from postman REST client tool.
Solution
1. Post verifying the provided credentials from postman, Create a new connection in EIC of type REST.
2. Use the below as the connection json:
{
"authentications": {
"acctAuth": {
"authType": "oauth2",
"url": "https://<ip-address>/rest/token",
"httpMethod": "POST",
"httpParams": {
"username": "username",
"password": "password"
},
"httpHeaders": {
"accept": "application/json"
},
"httpContentType": "application/json",
"errorPath": "error_msg",
"maxRefreshTryCount": 5,
"authHeaderName": "x-apikey",
"tokenResponsePath": "accesskey",
"accessToken": "accesskey=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx; secretkey=ccccccccccccccccccccccccccccccc;"
}
}
}
- The authHeaderName attribute signifies that the x-apikey field will be included in the header of subsequent call from this connector.
3. Below is the sample response of the /user api call.

As per the response below will be the json for importing accounts as accountparams:
"accountParams": {
"processingType": "SequentialAndIterative",
"connection": "acctAuth",
"call": {
"call1": {
"callOrder": 0,
"stageNumber": 0,
"http": {
"url": "https://<ipaddress>/rest/user?fields=username,firstname,lastname,email,status,authType,role,group",
"httpMethod": "GET",
"httpHeaders": {
"x-apikey": "${access_token}"
}
},
"listField": "response",
"keyField": "accountID",
"statusConfig": {
"active": "0",
"inactive": "1"
},
"colsToPropsMap": {
"accountID": "id~#~char",
"name": "username~#~char",
"status": "status~#~char",
"customproperty1": "email~#~char"
}
}
}
}
- The listfield is response as per the json output sample. And then name,accountid,status and customproperty1 is mapped respectively.
- The statusConfig provides mapping of the values for active and inactive accounts status as per feed value mapped in the status column.
- The accountparams section gets invoked and process the data when a application data import job with access type as Account is executed.
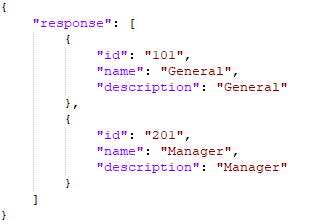
4. Now need to configure entitlementparams as per below response:
Group Response (Sample):
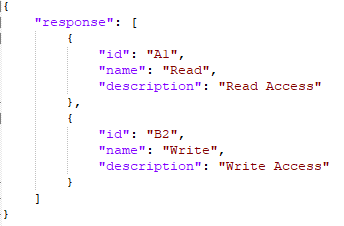
Role Response (Sample):
"entitlementParams": {
"processingType": "SequentialAndIterative",
"entTypes": {
"Group": {
"entTypeOrder": 0,
"call": {
"call1": {
"connection": "acctAuth",
"callOrder": 0,
"stageNumber": 0,
"http": {
"url": "https://<ipaddress>/rest/group?fields=id,name,description",
"httpMethod": "GET",
"httpHeaders": {
"x-apikey": "${access_token}"
}
},
"listField": "response",
"keyField": "entitlementID",
"colsToPropsMap": {
"entitlementID": "id~#~char",
"entitlement_value": "name~#~char",
"description": "description~#~char"
},
"disableDeletedEntitlements": true
}
}
},
"Roles": {
"entTypeOrder": 1,
"call": {
"call1": {
"connection": "acctAuth",
"callOrder": 0,
"stageNumber": 0,
"http": {
"url": "https://<ipaddress>/rest/role?fields=id,name,description",
"httpMethod": "GET",
"httpHeaders": {
"x-apikey": "${access_token}"
}
},
"listField": "response",
"keyField": "entitlementID",
"colsToPropsMap": {
"entitlementID": "id~#~char",
"entitlement_value": "name~#~char",
"description": "description~#~char"
},
"disableDeletedEntitlements": true
}
}
}
}
}
- disableDeletedEntitlements attribute tells to disable the entitlements not part of current response but are present in EIC under entitlements of specific type for the particular endpoint.
5. Till now we have imported account and entitlements individually, but to map the account to entitlements we need to define acctEntParams as per response of /user below:
"acctEntParams": {
"entTypes": {
"Group": {
"acctKeyField": "accountID",
"entKeyField": "en

titlementID",
"call": {
"call1": {
"processingType": "http",
"connection": "acctAuth",
"callOrder": 0,
"stageNumber": 0,
"http": {
"url": "https://<ipaddress>/rest/user?fields=id,group",
"httpMethod": "GET",
"httpHeaders": {
"x-apikey": "${access_token}"
}
},
"listField": "response",
"entListField": "group",
"acctIdPath": "id",
"entIdPath": "id"
}
}
},
"Roles": {
"acctKeyField": "accountID",
"entKeyField": "entitlementID",
"call": {
"call1": {
"processingType": "http",
"connection": "acctAuth",
"callOrder": 0,
"stageNumber": 0,
"http": {
"url": "https://<ipaddress>/rest/user?fields=id,role",
"httpMethod": "GET",
"httpHeaders": {
"x-apikey": "${access_token}"
}
},
"listField": "response",
"entListField": "role",
"acctIdPath": "id",
"entIdPath": "id"
}
}
}
}
}
- The acctEntParams and entitlementParams will be invoked and data will be processed when the application import job is run with access type as Access.
6. Now below are some sample of provisioning and deprovisioning json:
Enable Account JSON:
{
"call": [
{
"name": "call1",
"connection": "acctAuth",
"url": "https://<ipaddress>/rest/user/${account.accountID}",
"httpMethod": "PATCH",
"httpHeaders": {
"x-apikey": "${access_token}"
},
"httpParams": "{\"locked\":\"false\"}"
}
]
}
DisableAccountJSON:
{
"call": [
{
"name": "call1",
"connection": "acctAuth",
"url": "https://<ipaddress>/rest/user/${account.accountID}",
"httpMethod": "PATCH",
"httpHeaders": {
"x-apikey": "${access_token}"
},
"httpParams": "{\"locked\":\"true\"}"
}
]
}
Remove AccountJSON
{
"call": [
{
"name": "call1",
"connection": "acctAuth",
"url": "https://<ip-address>/rest/user/${account.accountID}",
"httpMethod": "DELETE",
"httpHeaders": {
"x-apikey": "${access_token}"
},
"httpContentType": "application/json",
"successResponses": {
"statusCode": [
200,
201,
204
]
}
}
]
}
References
https://docs.saviyntcloud.com/bundle/REST-v55x/page/Content/Developers-Handbook.htm


