- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- SSO integration with AzureAD
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SSO integration with AzureAD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/12/2022 01:08 AM
Hi team,
have configured SSO with Azure AD and uploaded the sp and idp inititiated files(from Azure) in saviynt EIC.
- Labels:
-
Other
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/12/2022 09:30 AM
Hello @sayeedaR ,
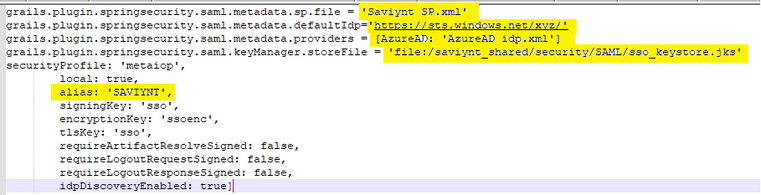
This happens when Saviynt is not able to generate SAML Authn request which is usually due to incorrect configuration in Authenticationconfig.Groovy file.
Please refer the documentation for the configuration steps :
Please ensure the below highlighted parameters are configured correctly.
Manikanta.S
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/27/2022 10:43 AM
Hi Manikanta,
Hope you are doing good!
Since we are trying to configure SSO with Customer tenant in EIC version 2022, We could be able to edit/Download the uploaded metadata and getting Attached), Do we have separate AuthenticationConfig file version 2022, I amy suspect the issue with metatda storing location or corrupted , Please advise
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/27/2022 12:45 PM
File location can you check with saviynt operations team with help of freshdesk
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/27/2022 01:18 PM
Thanks I have opened a support case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/27/2022 01:29 PM
Hello Suresh,
With the 2022 version you need not specify the file path, you can just mention the name of the uploaded SP/IDP/Keystore file.
Manikanta.S
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/27/2022
03:12 PM
- last edited on
10/27/2022
03:17 PM
by
![]() Dave
Dave
Thanks Manikanta, I have added the same in Config file and restarted below is the response, still no luck.
// IDP-1
<<<<<<< HEAD
<<<<<<< HEAD
=======
>>>>>>> c5d428454c32b73ae54ca4567e4820df8a34380d
grails.plugin.springsecurity.saml.metadata.sp.file = '/WEB-INF/classes/security/SAML/sp.xml'
grails.plugin.springsecurity.saml.metadata.defaultIdp='https://xxx.xxxxxxx.net/07497e85-9665-4d82-9d54-ea2496a522d9/'
grails.plugin.springsecurity.saml.metadata.providers = [AzureAD: '/WEB-INF/classes/security/SAML/idp.xml']
grails.plugin.springsecurity.saml.keyManager.storeFile = 'file:/WEB-INF/classes/security/SAML/sp.keystore.jks'
grails.plugin.springsecurity.saml.keyManager.storeFile = 'file:/WEB-INF/classes/security/SAML/keystore.jks'
<<<<<<< HEAD
=======
grails.plugin.springsecurity.saml.metadata.sp.file = '/WEB-INF/classes/security/SAML/sp.xml'
grails.plugin.springsecurity.saml.metadata.defaultIdp='https://xxx.xxxxxxx.net/07497e85-9665-4d82-9d54-ea2496a522d9/'
grails.plugin.springsecurity.saml.metadata.providers = [AzureAD: '/WEB-INF/classes/security/SAML/idp.xml']
grails.plugin.springsecurity.saml.keyManager.storeFile = 'file:/WEB-INF/classes/security/SAML/sp.keystore.jks'
grails.plugin.springsecurity.saml.keyManager.storeFile = 'file:/WEB-INF/classes/security/SAML/keystore.jks'
>>>>>>> 4a667bc2e82759c63983e5489d3e4a034b98e5e5
=======
>>>>>>> c5d428454c32b73ae54ca4567e4820df8a34380d
grails.plugin.springsecurity.saml.keyManager.storePass = 'changeit123'
grails.plugin.springsecurity.saml.keyManager.passwords = [ spsigned: 'changeit123' ]
grails.plugin.springsecurity.saml.keyManager.defaultKey = 'spsigned'
grails.plugin.springsecurity.saml.metadata.sp.defaults = [
securityProfile: 'metaiop',
local: true,
alias: 'matrixmedical-dev',
signingKey: 'spsigned',
encryptionKey: 'spsigned',
tlsKey: 'spsigned',
requireArtifactResolveSigned: false,
requireLogoutRequestSigned: false,
requireLogoutResponseSigned: false,
idpDiscoveryEnabled: true]
[This post has been edited by a moderator to remove personally identifiable information to abide by the Saviynt Community Terms of Use and Participation Guidelines.]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/27/2022 10:00 PM
You need specify full path
for example /opt/saviynt/tomcat/webapps/ECM/WEB-INF/classes/security/SAML/sp.xml
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/28/2022 06:38 AM - edited 10/28/2022 06:40 AM
Unfortunate no luck,
grails.plugin.springsecurity.saml.metadata.sp.file = '/opt/saviynt/tomcat/webapps/ECM/WEB-INF/classes/security/SAML/sp.xml'
grails.plugin.springsecurity.saml.metadata.providers = [AzureAD: '/opt/saviynt/tomcat/webapps/ECM/WEB-INF/classes/security/SAML/idp.xml']
grails.plugin.springsecurity.saml.keyManager.storeFile = 'file:/opt/saviynt/tomcat/webapps/ECM/WEB-INF/classes/security/SAML/keystore.jks'
securityProfile: 'metaiop',
local: true,
alias: 'matrixmedical-dev',
signingKey: 'spsigned',
encryptionKey: 'spsigned',
tlsKey: 'spsigned',
requireArtifactResolveSigned: false,
requireLogoutRequestSigned: false,
requireLogoutResponseSigned: false,
idpDiscoveryEnabled: true]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
10/30/2022 10:54 PM
Hello @sksuresh2k20 ,
With 2022 you need not mention the '/WEB-INF/classes/security/SAML/sp.xml'
You can only mention the file name as below:
grails.plugin.springsecurity.saml.metadata.sp.file = 'sp.xml'
grails.plugin.springsecurity.saml.metadata.defaultIdp='https://xyz.xyz.net/xxxxx-e309-4f91-94f5-72dffxxxxxx/'
grails.plugin.springsecurity.saml.metadata.providers = [test: 'AzureAD_idp.xml']
Manikanta.S
- Can we close pending task in Saviynt based on SNOW request status - IGA App integration ? in Identity Governance & Administration
- Google Saviynt Integration in Identity Governance & Administration
- RACF Integration in Identity Governance & Administration
- Reconcile AzureAD Application Entitlments owners using rest connector in Identity Governance & Administration
- Getting error while passing description to ITSM system in Identity Governance & Administration