- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- Re: SSO Configuration with new beta version not wo...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SSO Configuration with new beta version not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/11/2023 08:16 AM - edited 07/11/2023 08:17 AM
Hello Experts,
We are setting up the SSO for the first time and we have executed following steps :
- Imported Azure IDP XML under Identity Provider, mentioned SP Identity ID and Name ID .
- Configured the username attribute, sessions under General setting
- Copied the certificate of Azure AD from XML and prepared the certificate.
- Downloaded the default Saviynt certificate.
- Created the JKS of type "PKCS12" and added these 2 AAD and Default Saviynt Certificate.
Activated the SSO.
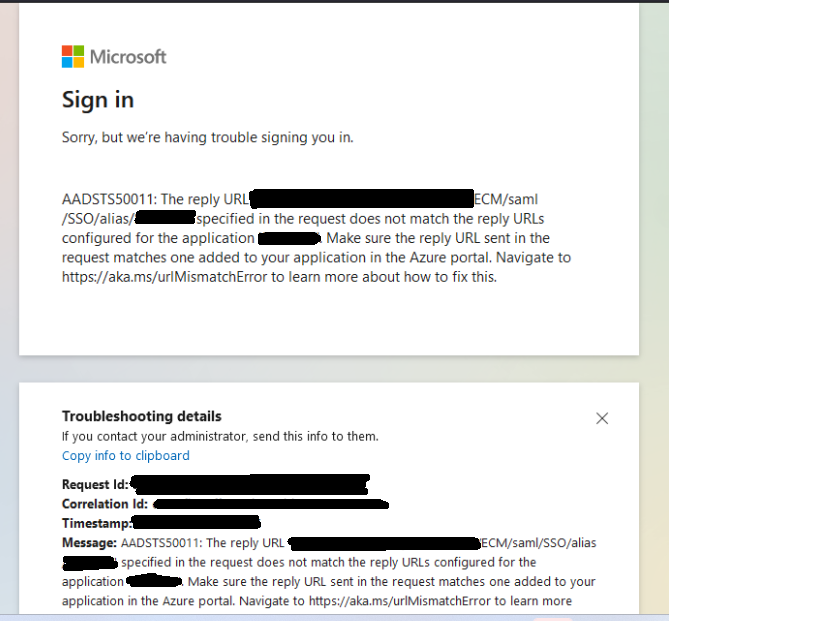
Below is the error we are getting:
Please help.
Regards,
Rahul
- Labels:
-
Other
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/12/2023 06:55 AM
Please check the Alias given in all the configurations are matching.
Also please validate the URL's configured in the configuration files.
Regards
Rakesh M Goudar
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/13/2023 03:55 AM
Hi @rahul_p
The error message (AADSTS50011) indicates that the specified reply URL (ECM/saml/SSO/alias/) in the request does not match the configured reply URLs for the application in the Azure portal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/13/2023 04:16 AM
Hello @DixshantValecha @RakeshMG ,
Thank you both for your reply.
We will check and get back to you.
Regards,
Rahul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/18/2023 04:57 AM
Hi @rahul_p please try and make sure that the Entity ID(Identifier) is matching with what you have provided in the reply URL in Azure AD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/19/2023 04:51 AM
Hello @sowmyashiva @DixshantValecha @RakeshMG ,
We did execute the steps mentioned in the document which are in high-level are import the certificates and idp XML as per Saviynt document which is not working.
- We used default SP certificate which comes with Saviynt.
- We did not change anything under Show Advanced Configurations.
- Under Setup IDP, we mentioned entityID, URL.
- Under the IDP setting we added the name, selected IDP file and attribute(after clicked on save and opened this setting again, it doesn't show any IDP file selected.)
- activated SSO.
Can anybody point here, what went wrong?
Regards,
Rahul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/20/2023 06:44 AM
Hi,
To troubleshoot this error, you can try the following steps:-
#Check the validity and consistency of the certificates used by both Azure AD and Saviynt. You can use tools like Fiddler or Charles to inspect the HTTP requests and responses and extract the certificates. You can also use online tools like >samltool.com/validate_response.php to validate the SAML response and its signature.
#Look for any invalid characters or whitespace in the SAML response that could invalidate the signature. You can use online tools like >xmlvalidation.com to check the XML syntax and format.
#Check Logs and Error Messages:
- Check the logs on both the IDP and Saviynt side for any error messages or hints about what might be going wrong.
Test with Different Browsers:
- Sometimes, SSO issues can be browser-specific. Try testing with different browsers to see if the problem persists.
I hope this helps you resolve your issue. If you need more assistance, please let us know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/21/2023 03:20 AM
@rahul_p did you compare the replyURL shown in the logs with what is configured in the AAD application. Do they match? If not, then you need to update it in AAD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/03/2023 06:42 AM - edited 08/03/2023 06:42 AM
Hello,
Now, SSO started working after updating the reply URL which was different and then it was communicated to us incorrectly.
But now SSO working only incognito mode or when we clear browser history then only its working.
Any comments?
Regards,
Rahul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/08/2023 05:11 AM
As for the new issue you're facing, where SSO only works in incognito mode or after clearing the browser history, this behavior might be related to caching or cookies stored in the browser. Here are a few things you can consider and steps you can take to address this:
Browser Cache: Sometimes, browsers can cache certain information, including SSO-related data. This might cause conflicts when trying to authenticate. Try clearing the cache of the browser (not just the history) and then attempt to use SSO again.
Cookies: SSO often relies on cookies to manage authentication sessions. Incorrectly stored or outdated cookies can cause authentication issues. Clear all cookies related to the SSO provider's domain and try again.
Browser Extensions: Some browser extensions or plugins might interfere with SSO functionality. Try disabling any extensions that might affect web interactions and see if the issue persists.
- Campaign Emails Not being triggered V23.5 in Identity Governance & Administration
- Assistance Required with Error Handling and Log Verbosity in Saviynt v24.3 in Identity Governance & Administration
- Modify delegate not working in Identity Governance & Administration
- Error sending email using Notify option from Certifications page in Identity Governance & Administration
- Tickets not created for Disable account and Remove access tasks. in Identity Governance & Administration