- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- SOAP Workday Grant Access not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SOAP Workday Grant Access not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/08/2023
11:27 AM
- last edited on
12/11/2023
01:19 PM
by
![]() Dave
Dave
Hi,
I have the following Grant Access JSON setup exactly how the workday SOAP connector provided and while the access task gets completed successfully the role is not getting provisioned to Workday. No errors in the logs as well.
[{
"CONNECTION": "addRemoveAccess",
"REQUESTXML": "<soapenv:Envelope xmlns:soapenv=\"http://schemas.xmlsoap.org/soap/envelope/\" xmlns:bsvc=\"urn:com.workday/bsvc\"> <soapenv:Header> <wsse:Security soapenv:mustUnderstand=\"1\" xmlns:wsse=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd\" xmlns:wsu=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd\"> <wsse:UsernameToken wsu:Id=\"UsernameToken-64DBF26FBA30D3CCB6146964280369918\"> <wsse:Username>${USERNAME}</wsse:Username> <wsse:Password Type=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText\">${PASSWORD}</wsse:Password> <wsse:Nonce EncodingType=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary\">lLP+oysknDXxg0ZcnRTUXg==</wsse:Nonce> </wsse:UsernameToken> </wsse:Security> </soapenv:Header> <soapenv:Body> <bsvc:Put_Assign_User-Based_Security_Groups_Request bsvc:version=\"v31.0\"> <bsvc:Assign_User-Based_Security_Groups_Data> ${com.saviynt.ecm.identitywarehouse.domain.Entitlement_values.findAllByEntitlement_valueInListAndEntitlementtypekey(allEntitlementMap.get('Security-Groups'), entTask.entitlement_valueKey.entitlementtypekey).findAll{it.entitlement_glossary?.equalsIgnoreCase('User-Based Security Group')}?.size() > 0 ? com.saviynt.ecm.identitywarehouse.domain.Entitlement_values.findAllByEntitlement_valueInListAndEntitlementtypekey(allEntitlementMap.get('Security-Groups'), entTask.entitlement_valueKey.entitlementtypekey).findAll{it.entitlement_glossary?.equalsIgnoreCase('User-Based Security Group')}.collect { '<bsvc:User-Based_Security_Group_Reference bsvc:Descriptor=\"?\"><bsvc:ID bsvc:type=\"Tenant_Security_Group_ID\">' + it.entitlementID + '</bsvc:ID></bsvc:User-Based_Security_Group_Reference>' }.join('') : '<bsvc:User-Based_Security_Group_Reference bsvc:Descriptor=\"?\"></bsvc:User-Based_Security_Group_Reference>'} <bsvc:Workday_Account_Reference bsvc:Descriptor=\"?\"> <bsvc:ID bsvc:type=\"System_User_ID\">${account.name}</bsvc:ID> </bsvc:Workday_Account_Reference> </bsvc:Assign_User-Based_Security_Groups_Data> </bsvc:Put_Assign_User-Based_Security_Groups_Request></soapenv:Body></soapenv:Envelope>"
}]
I used the same payload in postman and was able to provision a user based security group in workday.
Thanks,
Umang
[This post has been edited by a Moderator to merge two posts.]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/11/2023 09:58 PM - edited 12/11/2023 10:13 PM
Hello @umang28,
Is this a new implementation?
why are using Wokrday-Soap 1.0 not the Workday connector 2.0? You should be using the workday connector 2.0 , if this is the new implementation as it provides more functionalities compare to workday 1.0
also you are passing the ${USERNAME} instead please try with '+USERNAME+' or ${user.username}.
Thanks
For Ref :- https://docs.saviyntcloud.com/bundle/WD2-v23x/page/Content/Provisioning.htm#top
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/12/2023 09:07 AM - edited 12/12/2023 09:45 AM
I am using the SOAP Workday connector 1.0 "Workday-SOAP" to support multiple endpoints in the CONNECTIONJSON. Could you provide a working body of the grant access JSON? When I use '+USERNAME+' I get an invalid username or password error
Thanks,
Umang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/12/2023 12:52 PM
I tried the following way and got this error groovy.lang.MissingPropertyException: No such property: entitlementID for class: java.lang.String
[
{
"CONNECTION":"addRemoveAccess",
"REQUESTXML":"${user.employeeType != 'Employee' && user.employeeid != null && user.employeeid != '' ? ('<soapenv:Envelope xmlns:soapenv=\"http://schemas.xmlsoap.org/soap/envelope/\" xmlns:bsvc=\"urn:com.workday/bsvc\"> <soapenv:Header> <wsse:Security soapenv:mustUnderstand=\"1\" xmlns:wsse=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd\" xmlns:wsu=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd\"> <wsse:UsernameToken wsu:Id=\"UsernameToken-64DBF26FBA30D3CCB6146964280369918\"> <wsse:Username>' +USERNAME + '</wsse:Username> <wsse:Password Type=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText\">' +PASSWORD+'</wsse:Password> <wsse:Nonce EncodingType=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary\">lLP+oysknDXxg0ZcnRTUXg==</wsse:Nonce> </wsse:UsernameToken> </wsse:Security> </soapenv:Header> <soapenv:Body> <bsvc:Put_Assign_User-Based_Security_Groups_Request bsvc:version=\"v38.2\"> <bsvc:Assign_User-Based_Security_Groups_Data> <bsvc:User-Based_Security_Group_Reference> <bsvc:ID bsvc:type=\"WID\">'+entitlement_value.entitlementid+'</bsvc:ID> </bsvc:User-Based_Security_Group_Reference> <bsvc:Workday_Account_Reference> <bsvc:ID bsvc:type=\"System_User_ID\">'+user.username+'</bsvc:ID> </bsvc:Workday_Account_Reference> </bsvc:Assign_User-Based_Security_Groups_Data> </bsvc:Put_Assign_User-Based_Security_Groups_Request> </soapenv:Body> </soapenv:Envelope>') : ''}",
"CUSTOM_CONFIG1":{
"WSCALLDELAYTIMESEC":"0",
"CONNECTTIMEOUTINSEC":"200",
"READTIMEOUTINSEC":"60"
}
}
]
How can we map the WID?
Thanks,
Umang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/15/2023 07:26 AM
Hello @umang28,
Whats the bussiness use-case for the multiple endpoints in the CONNECTIONJSON.
As suggested earlier, Instead you may go with Workday connector 2.0.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/15/2023 07:37 AM
Hi @sudeshjaiswal That is not possible since we have configured to manage the lifecycle of contingent workers in workday which includes creation, updates, terminations and re-hires while calling different operations/endpoints only supported by the Workday-SOAP connector.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/12/2023 09:06 PM
Hello @umang28,
Please try with the below sample,
[
{
"CONNECTION": "login",
"REQUESTXML": "
<soapenv:Envelope
xmlns:soapenv=\"http://schemas.xmlsoap.org/soap/envelope/\"
xmlns:bsvc=\"urn:com.workday/bsvc\">
<soapenv:Header>
<wsse:Security soapenv:mustUnderstand=\"1\"
xmlns:wsse=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd\"
xmlns:wsu=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd\">
<wsse:UsernameToken wsu:Id=\"UsernameToken-64DBF26FBA30D3CCB6146964280369918\">
<wsse:Username>${USERNAME}</wsse:Username>
<wsse:Password Type=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText\">${PASSWORD}</wsse:Password>
<wsse:Nonce EncodingType=\"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary\">lLP+oysknDXxg0ZcnRTUXg==</wsse:Nonce>
</wsse:UsernameToken>
</wsse:Security>
</soapenv:Header>
<soapenv:Body>
<bsvc:Put_Assign_User-Based_Security_Groups_Request bsvc:version=\"v31.0\">
<bsvc:Assign_User-Based_Security_Groups_Data> ${com.saviynt.ecm.identitywarehouse.domain.Entitlement_values.findAllByEntitlement_valueInListAndEntitlementtypekey(allEntitlementMap.get('Security-Groups'), entTask.entitlement_valueKey.entitlementtypekey).findAll{it.entitlement_glossary?.equalsIgnoreCase('User-Based Security Group')}?.size() > 0 ? com.saviynt.ecm.identitywarehouse.domain.Entitlement_values.findAllByEntitlement_valueInListAndEntitlementtypekey(allEntitlementMap.get('Security-Groups'), entTask.entitlement_valueKey.entitlementtypekey).findAll{it.entitlement_glossary?.equalsIgnoreCase('User-Based Security Group')}.collect { '
<bsvc:User-Based_Security_Group_Reference bsvc:Descriptor=\"?\">
<bsvc:ID bsvc:type=\"Tenant_Security_Group_ID\">' + it.entitlementID + '</bsvc:ID>
</bsvc:User-Based_Security_Group_Reference>' }.join('') : '
<bsvc:User-Based_Security_Group_Reference bsvc:Descriptor=\"?\"></bsvc:User-Based_Security_Group_Reference>'}
<bsvc:Workday_Account_Reference bsvc:Descriptor=\"?\">
<bsvc:ID bsvc:type=\"System_User_ID\">${account.accountID}</bsvc:ID>
</bsvc:Workday_Account_Reference>
</bsvc:Assign_User-Based_Security_Groups_Data>
</bsvc:Put_Assign_User-Based_Security_Groups_Request>
</soapenv:Body>
</soapenv:Envelope>"
}
]Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/13/2023 02:31 PM
I tried the same and provided the details initially when creating this post. Few other ways I tried were either by binding the variables, hardcoding them in the payload, working payload from postman but all resulted in getting the Provisioning Metadata as an empty string (logs attached). Although it was able to do the entitlements mapping correctly.
The create, enable, update, disable JSONS are configured and works perfectly fine but the grant access is causing the role provisioning in PROD not to work and would need a quick resolution.
Could you also let me know where the '+it.entitlementID+' value is getting pulled from? Attaching couple of different JSONS I tried for your reference. Let me know if we can get on a call too?
Thanks,
Umang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/13/2023 10:45 PM
Hello @umang28,
Can you please confirm if you are getting the Security_Group_Type in the entitlment glossary, if not which attribute you have mapping this information in the Access Import.
You will have to use that attribute in below highlighted attribute.
entTask.entitlement_valueKey.entitlementtypekey).findAll{it.entitlement_glossary?.equalsIgnoreCase('User-Based Security Group')}?.size() > 0 ? com.saviynt.ecm.identitywarehouse.domain.Entitlement_values.findAllByEntitlement_valueInListAndEntitlementtypekey(allEntitlementMap.get('Security-Groups'), entTask.entitlement_valueKey.entitlementtypekey).findAll{it.entitlement_glossary?.equalsIgnoreCase('User-Based Security Group')}.collect {
You need the replace the atttibute with the exact mapping you have mentioned in the accessimport.
Also would like to confirm if you "Tenant_Security_Group_ID" is infact mapped to entitlementID in saviynt. Please check in the access import mapping.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
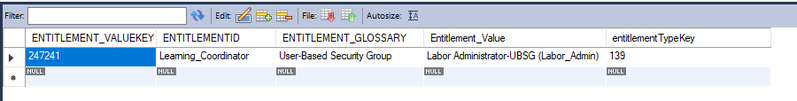
12/14/2023 09:47 AM - edited 12/14/2023 01:17 PM
Groups are imported through the RAAS API. Yes, I believe it is pulling that data from the entitlement_values table right? Here are the specific details of the group:
Data seems to be correct, hence, it was able to pull the Existing Entitlements, Existing Entitlements Map and allEntitlementMap. If I set an incorrect entitlementID value in the entitlementID column, it does not throw any validation error but if hardcode an incorrect entitlementID in the payload it then throws the validation error as expected (logs). Plus hardcoding the correct entitlementID in the payload should be straight forward in provisioning the group but it doesn't seem to like anything.
Could you also let me know the location where the default payloads of each JSONs of the workday connector are defined on the server?
Thanks,
Umang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/19/2023 01:41 AM
Hi Umang,
Were you able to resolve it?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/20/2023 01:06 AM - edited 12/20/2023 01:43 AM
Hello @umang28 ,
Can you please provide the account ,access import connection parameters.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/20/2023 12:19 PM
Hi @sudeshjaiswal @gauravchandok The payload is indeed working after I got a confirmation from Workday that the group was provisioned, however, while I was running the import job _SAV_AccountsToSecurityGroups_ , all the groups were getting removed from the user in Saviynt due to the incorrect data.
We are using the Hybrid workday connector 2.0 for importing purposes and based on the documentation: Non-editable Default Access Mapping are as follows:
{
"Security Group": {
"ImportMapping": {
"ENTITLEMENTID": "wd:Security_Group.wd:ID[0].content~#~char",
"ENTITLEMENT_VALUE": "wd:Security_Group.wd:Descriptor~#~char",
"ENTCLASS": "wd:Security_Group_Type.wd:Descriptor~#~char",
"STATUS": "wd:Inactive~#~char"
}
},Which means ENTITLEMENTID should be mapped to WID type and not the Tenant_Security_Group_ID which is incorrectly mentioned in the default payload of the connector.
Thanks,
Umang
- UPDATE ACCESS ENDDATE DOESNT WORK in Identity Governance & Administration
- Campaign Emails Not being triggered V23.5 in Identity Governance & Administration
- Assistance on Query || Reportee Access Details in Identity Governance & Administration
- createrequest via the API for adding user to roles in Identity Governance & Administration
- Updating Logo for Enterprise Role || v23.11 in Identity Governance & Administration