- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- Adding a user to Teams Group
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Adding a user to Teams Group
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/25/2023 07:00 AM
Hello All,
We have a requirement to add a user to one of their Teams group. We have to do this every time a new user onboards from Workday, probably as a birthright provisioning. Could you please suggest how can we achieve this and what are all the saviynt modules needed for this.
Thank you in advance for your help
- Labels:
-
Admin
-
Need Information
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/25/2023 07:02 AM - edited 07/25/2023 07:03 AM
Hi @Suresh1 ,
Setup a technical rule with the below :
1. A condition that satisfies the user creation
2. Select the Teams group as an entitlement to be added as a birthright access
3. Select the "Birthright" option under the technical rules.
Once all the above 3 are done, upon new user creation, the teams group will be added as a birthright access.
Note: The user should already have an account in Teams endpoint for this access to be added.
Naveen Sakleshpur
If this reply answered your question, please click the Accept As Solution button to help future users who may have a similar problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/25/2023 07:12 AM - edited 07/25/2023 07:14 AM
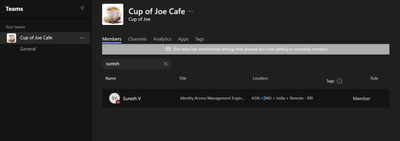
@naveenss , Do we have to integrate Teams as an endpoint in Saviynt ? if yes, Which type of connector should be used here ?
Just to be clear on the requirement User needs to be added as a member of a Teams group chat in Microsoft Teams application as shown below
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/25/2023 07:18 AM
Hi @Suresh1 ,
Just to clarify a few points!
Do you already have an Azure AD integration in place? If yes, do you have the MS teams imported as entitlements?
Naveen Sakleshpur
If this reply answered your question, please click the Accept As Solution button to help future users who may have a similar problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/01/2023 07:58 AM
Hi @naveenss ,
We do have Azure AD integrated with Saviynt. But we dont have MS teams entitlements imported
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
07/25/2023 04:12 PM
Yes you will have to integrate Azure as an endpoint in Saviynt before you follow the steps suggested by @naveenss
Devang Gandhi
If this reply answered your question, please Accept As Solution and give Kudos to help others who may have a similar problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/02/2023 10:50 AM
We do have Azure AD integrated with Saviynt. But we dont have MS teams entitlements imported
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/02/2023 10:10 PM
can you please share your access import configurations?
Naveen Sakleshpur
If this reply answered your question, please click the Accept As Solution button to help future users who may have a similar problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/03/2023 07:26 AM
Hi @naveenss
Below is the ImportAccountEntJSON configured.
{
"accountParams": {
"connection": "userAuth",
"processingType": "SequentialAndIterative",
"statusAndThresholdConfig": {
"deleteLinks": true,
"accountThresholdValue": 20000,
"correlateInactiveAccounts": false,
"inactivateAccountsNotInFile": true,
"deleteAccEntForActiveAccounts ": true
},
"call": {
"call1": {
"callOrder": 0,
"stageNumber": 0,
"showJobHistory": true,
"showResponse": true,
"http": {
"url": "https://graph.microsoft.com/v1.0/users/?$filter=extension_2986e93e5cf3416295d15c40f7c5d65f_ktbAccoun...",
"httpContentType": "application/json",
"httpMethod": "GET",
"httpHeaders": {
"Authorization": "${access_token}",
"Accept": "application/json"
}
},
"listField": "value",
"keyField": "accountID",
"statusConfig": {
"active": "true",
"inactive": "false"
},
"colsToPropsMap": {
"accountID": "id~#~char",
"name": "userPrincipalName~#~char",
"displayname": "displayName~#~char",
"status": "accountEnabled~#~char",
"customproperty1": "givenName~#~char",
"customproperty2": "surname~#~char",
"customproperty3": "businessPhones~#~char",
"customproperty4": "mail~#~char",
"customproperty5": "mobilePhone~#~char",
"customproperty6": "officeLocation~#~char",
"customproperty8": "userType~#~char",
"customproperty9": "jobtitle~#~char",
"customproperty10": "accountEnabled~#~char",
"customproperty11": "onPremisesSyncEnabled~#~char",
"customproperty12": "onPremisesImmutableId~#~char",
"customproperty14": "onPremisesLastSyncDateTime~#~char",
"customproperty15": "onPremisesSecurityIdentifier~#~char",
"customproperty16": "city~#~char",
"customproperty17": "country~#~char",
"customproperty18": "department~#~char",
"customproperty19": "usageLocation~#~char",
"customproperty20": "employeeId~#~char",
"customproperty21": "extension_2986e93e5cf3416295d15c40f7c5d65f_ktbssousername~#~char",
"customproperty23": "extension_44fd69891c9b4e39b64630a55e6f27a8_O365license~#~char",
"customproperty24": "extension_44fd69891c9b4e39b64630a55e6f27a8_WDWorkerType~#~char",
"customproperty29": "mailNickname~#~char",
"customproperty31": "STORE#ACC#ENT#MAPPINGINFO~#~char"
},
"pagination": {
"nextUrl": {
"nextUrlPath": "${(response?.completeResponseMap?.get('@odata.nextLink')==null)? null : response?.completeResponseMap?.get('@odata.nextLink')}"
}
}
}
}
},
"entitlementParams": {
"connection": "userAuth",
"processingType": "SequentialAndIterative",
"entTypes": {
"AADGroup": {
"entTypeOrder": 0,
"entTypeLabels": {},
"call": {
"call1": {
"callOrder": 0,
"stageNumber": 0,
"http": {
"url": "https://graph.microsoft.com/v1.0/groups/microsoft.graph.group",
"httpHeaders": {
"Authorization": "${access_token}",
"Accept": "application/json"
},
"httpContentType": "application/json",
"httpMethod": "GET"
},
"listField": "value",
"keyField": "entitlementID",
"colsToPropsMap": {
"entitlementID": "id~#~char",
"entitlement_value": "displayName~#~char",
"customproperty1": "createdDateTime~#~char",
"customproperty2": "securityIdentifier~#~char",
"customproperty3": "mailNickname~#~char",
"customproperty4": "mailEnabled~#~char",
"customproperty6": "securityEnabled~#~char",
"customproperty7": "mail~#~char",
"acctEntMappingInfoColumnFromEnt": "STORE#ACC#ENT#MAPPINGINFO~#~char"
},
"pagination": {
"nextUrl": {
"nextUrlPath": "${(response?.completeResponseMap?.get('@odata.nextLink')==null)? null : response?.completeResponseMap?.get('@odata.nextLink')}"
}
},
"disableDeletedEntitlements": true
}
}
}
}
},
"acctEntParams": {
"connection": "userAuth",
"entTypes": {
"AADGroup": {
"call": {
"call1": {
"callOrder": 0,
"stageNumber": 0,
"processingType": "httpEntToAcct",
"http": {
"httpHeaders": {
"Authorization": "${access_token}"
},
"url": "https://graph.microsoft.com/v1.0/groups/microsoft.graph.group/${id}/members",
"httpContentType": "application/x-www-form-urlencoded",
"httpMethod": "GET"
},
"listField": "value",
"entKeyField": "entitlementID",
"acctIdPath": "id",
"acctKeyField": "accountID",
"pagination": {
"nextUrl": {
"nextUrlPath": "${(response?.completeResponseMap?.get('@odata.nextLink')==null)? null : response?.completeResponseMap?.get('@odata.nextLink')}"
}
}
}
}
}
}
}
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/03/2023 11:24 PM
Hi @Suresh1 are you using REST connector for imports?
Naveen Sakleshpur
If this reply answered your question, please click the Accept As Solution button to help future users who may have a similar problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/09/2023 03:25 AM
Yes, @naveenss
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/09/2023 04:02 AM
@Suresh1 any reason you are not using the OOTB AzureAD connector? As per the best practices, REST connector should be used only for provisioning.
For imports, you must use Azure AD connector.
Naveen Sakleshpur
If this reply answered your question, please click the Accept As Solution button to help future users who may have a similar problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
08/09/2023 09:36 AM
Hi @naveenss ,
We were using OOTB Azure AD connector earlier and team identified couple of issues with its import timing and job getting struck several times and other parameters so we switched to custom REST connector again.
Below are the FD tickets raised by our team on issues of Azure AD connector.
https://saviynt.freshdesk.com/support/tickets/1354413
https://saviynt.freshdesk.com/support/tickets/791812
- CyberArk Safe creation in Identity Governance & Administration
- Remove User From AD Groups 14 days After Termination in Identity Governance & Administration
- provision AD based auth group while requesting new account in Identity Governance & Administration
- Send Monthly email notification to individual Disconnected application owner in Application Access Governance
- How to control SSO PingID oneaccount using AD groups in Identity Governance & Administration