- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- How to bulk update EndDate (account_entitlements1)...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to bulk update EndDate (account_entitlements1) via Analytics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/12/2024 07:15 AM
Hi All,
We have an application where Account's access should have End Date. So End Date has been made mandatory in Saviynt Form. Once EndDate is set then it is visible in Saviynt GUI >> Application's Account >> Associated Entitlement >> Access Name 1 >> End Date.
END DATE is needed as access deprovisioning is triggered on that. But existing accounts (in Application) does not have any End Date set.
Once imported, I can use Enhanced Job Query to insert End Date, but deprovisioning Job still won't trigger as it also checks ARSTASKKEY value, which would be empty as this End Date is not inserted by Saviynt.
How can I insert End Date in App Account's access with ARSTASKKEY ?
Is there any way I can use Analytics to check End Date, if missing then raise 'Update Access End Date' as default task ? with this I would be able to set some default End Date value and also would have ARSTASKKEY value updated in account_entitlements1 table ?
Please provide any help or suggestions to achieve this.
Thanks,
- Labels:
-
Access Request
-
Analytics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/12/2024 01:53 PM
You can run baseline job for taskkey & update end date from enhanced query
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/14/2024 11:44 PM
Hi Rushikesh,
Thanks for response!!
Can you please explain bit more on baseline job for taskkey update.
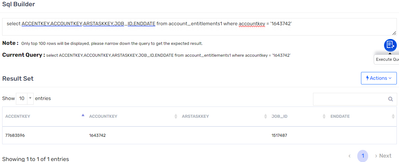
I am getting below data when imported sample accounts (existing) from Application, where both End Date and ARSTASKKEY is missing:-
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/15/2024 07:35 AM
Under Endpoints - Click on Baseline application
Baseline Application/Re-Baseline Application | Baselining of an application is the process of identifying rogue accounts or accesses, and taking measures for onboarding them accordingly. A baselining operation is performed by default for every application that is imported within Saviynt. You can also baseline an application manually by clicking Baseline Application for an endpoint by navigating to Admin > Security System > Endpoints. Saviynt also provides a Re-Baseline Application option that reviews any incremental changes within the application, due to which there could be a new set of rogue accesses. As the name suggests, re-baselining can be performed for applications that have already been baselined before. Video: Enhanced Application Baselining For re-baselining an already baselined application, click the Re-Baseline Application option for an endpoint by navigating to Admin > Security System > Endpoints. For re-baselining an already baselined application, perform the following steps:
The role-user and rule user repair options have been included in Re-Baselining to ensure that all entitlements are removed for users when they are no longer part of a role or they do not match the rule conditions. They help in scenarios such as a faulty import interrupting the role to user or rule to user relationships. The ‘i' icon next to the Baseline Application or Re-Baseline Application option to displays details such as the generated ‘arstaskkey’, the user who initiated the baseline application process, the date, and the number of accounts and entitlements that are baselined. For more information about 'arstaskkey’, see the Accounts Table in the Enterprise Identity Cloud Schema Guide. EIC also provides an out-of-band access detection functionality that detects and revokes accesses that are assigned by the target system. Based on the baseline or re-baseline results, you can choose the DeprovisionAccess or Deprovision Access and Re-create Access Request option from Action for Out of Band Access Detection for the rogue accounts or accesses found. To know more, see Configuring the detection of out-of-band access for endpoints in the Knowledge Base Articles. |
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Analytics email to managers about their subordinates in Identity Governance & Administration
- Assistance on Query || Reportee Access Details in Identity Governance & Administration
- Runtime Analytics - Data Displayed Error in Identity Governance & Administration
- Actionable Analytic- How to add multiple Entitlements in Identity Governance & Administration
- update ae1.enddate (access end date) in Identity Governance & Administration