- Saviynt Forums
- Saviynt Exchange
- Community Sourced Integrations
- ForgeRock - CIAM Integration Guide
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Notify a Moderator
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Notify a Moderator
02/12/2024 09:22 PM - edited 02/13/2024 01:03 AM
Disclaimer
The integration was created by Saviynt community users.. The integration is available “as is” and falls under standard connectors support for REST, SOAP, JDBC, LDAP, PowerShell, Jar, and Saviynt Connector Framework.
- Preface
- Audience
- Introduction
- Supported Features
- Understanding the Integration between EIC and ForgeRock - CIAM
- Integration Architecture
- Creating a Connection
- Using the ForgeRock - CIAM Integration
- Troubleshooting
Preface
This guide describes the integration between Saviynt Enterprise Identity Cloud (EIC) and ForgeRock - CIAM.
Audience
This guide is intended for administrators and target application integration teams responsible for implementing a secure integration service with ForgeRock - CIAM.
Introduction
ForgeRock Customer Identity and Access Management (CIAM) enables you to give your customers a frictionless and highly personalized online experience. With advanced security, consent management, privacy protections, and self-service, ForgeRock CIAM helps you acquire customers faster, improve retention, and protect customer data.
This enables the business to deliver a great experience to customers and to protect their user data.
Business wants to integrate ForgeRock - CIAM with Saviynt for automated user creation/management in ForgeRock - CIAM.
The ForgeRock - CIAM connector enables you to seamlessly integrate with ForgeRock - CIAM to manage the user lifecycle and govern access to their accounts and workspaces.
For more information about different connectors in EIC, see Connectors Documentation.
Supported Features
The ForgeRock - CIAM integration supports the following features:
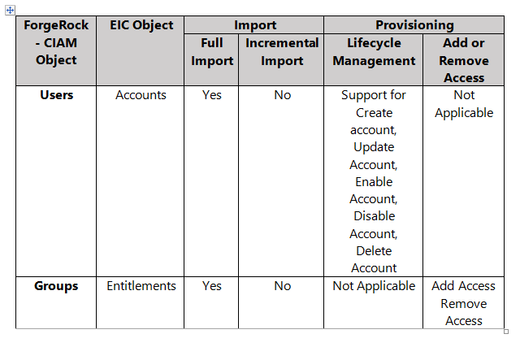
Understanding the Integration between EIC and ForgeRock - CIAM
You must create an integration between EIC and the collaboration platform hosted by the target application to perform import, provisioning, and de-provisioning tasks. The following components are involved in the integration:
- Objects are imported as entitlement types into EIC.
- Security System represents the connection between EIC and the target application.
- It comprises an endpoint, which is the target application for which you want EIC to manage the identity repository.
- It provides application instance abstraction from connectivity including high-level metadata. For more information about creating a security system, see Creating a Security System.
- Endpoint is an instance of an application within the context of a security system.
- It is the target application or application from which the connector imports the data and performs provisioning or de-provisioning of identity objects, such as users, accounts, and entitlements.
- It is mandatory to create an endpoint after creating the security system.
You can associate a single security system with multiple endpoints if the deployment involves modeling multiple isolated virtual applications (based on sets of specific entitlements according to certain categories) within a single application instance. For more information about creating an endpoint, see Creating an Endpoint for the Security System.
- The connector is a software component that enables communication between EIC and the target application. It provides a simplified integration mechanism where in some instances you only need to create a connection with minimal connectivity information for your target application. The REST connector is used for importing, provisioning accounts, and accessing through the REST APIs. For more information about creating a connection, see Creating a Connection.
- Job Scheduler is a software component that executes a job based on the configured schedule to perform import or provisioning operations from EIC.
When a provisioning job is triggered, it creates provisioning tasks in EIC. When these tasks are completed, the provisioning action is performed on the target application through the configured connector. If you want to instantly provision requests for completing the tasks without running the provisioning job, you must enable Instant Provisioning at the security system level and the Instant Provisioning Tasks global configuration. For more information about the jobs used by the connectors in the ForgeRock - CIAM integration.
Integration Architecture
EIC uses a REST connection for integrating with ForgeRock - CIAM for importing data and for performing provisioning and de-provisioning tasks.
The following diagram illustrates the integration architecture and communication with the target application.
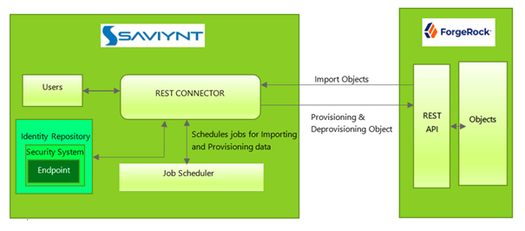
- Standard REST connector using SCIM protocol is used to connect ForgeRock - CIAM application to Saviynt.
- REST API calls are made through REST connector to execute multiple operations (i.e. Import accounts / Import Access /Create Account/ Update Account / Disable Account / Add Access /Remove Access / Enable account)
- The REST integration enables you to gain visibility, manage user life cycle, and govern access for the data available in the REST endpoint.
Account reconciliation:
- Saviynt is importing all the user accounts from ForgeRock - CIAM.
Below are the account attributes details which are getting imported from ForgeRock - CIAM.
ForgeRock CIAM AccountAttribute | SaviyntAccountAttribute |
accountID | _id |
name | |
displayName | |
customproperty1 | sn |
customproperty2 | givenName |
customproperty3 | |
status | accountStatus |
customproperty4 | frIndexedString3 |
customproperty5 | _id |
customproperty6 | frUnindexedString3 |
customproperty7 | accountStatus |
Access reconciliation
- Saviynt is importing all Groups (entitlements) from ForgeRock - CIAM.
Below are the entitlement attribute details which are imported from ForgeRock - CIAMinto Saviynt.
ForgeRock CIAM Entitlement Attribute | Saviynt Entitlement Attribute |
entitlementID | _id |
entitlement_value | name |
displayname | name |
customproperty1 | _id |
customproperty2 | _rev |
description | description |
Creating a Connection
Connection refers to the configuration setup for connecting EIC to target applications. For more information about the procedure to create a connection, see Creating Connections.
Understanding the Configuration Parameters
While creating a connection, you must specify connection parameters that the connector uses to connect with the target application, define the type of operations to perform, the target application objects against which those operations are performed, and the frequency of performing them. In addition, you can view and edit attribute mappings between EIC and the target application, predefined correlation rules, and provisioning jobs and import jobs.
Importing Connection Package
The Connection Package helps you build the connection with pre-defined JSONs, this can be used if your tenant does not already have out of the box connection templates available. Here are the steps to import the ForgeRock - CIAM connection package.
- Download the connection package.
- Navigate to Admin → Transport → select Import Package.
- Browse the downloaded package and Import.
- Navigate to Admin → Connections → Select “ForgeRock - CIAM ” Connection.
- Edit the connection with your ForgeRock - CIAMTenant Details.
Connection JSON
The connection JSON cannot be embedded in the Connection Package. Hence attaching the Connection JSON separately
| { "authentications": { "userAuth": { "authType": "oauth2", "url": "https://<URL>/am/oauth2/access_token", "httpMethod": "POST", "httpParams": { "client_id": "<Client Id>", "client_secret": "<Client Secret>", "password": "<Password>", "grant_type": "password", "scope": "fr:idm:*", "username": "<Username>" }, "httpHeaders": { "Content-Type": "application/x-www-form-urlencoded" }, "httpContentType": "application/x-www-form-urlencoded", "expiryError": "ExpiredAuthenticationToken", "authError": [ "InvalidAuthenticationToken", "Missing parameter" ], "timeOutError": "Read timed out", "errorPath": "error.error_description", "maxRefreshTryCount": 5, "tokenResponsePath": "access_token", "tokenType": "Bearer", "retryFailureStatusCode": [ 401 ], "accessToken": "Bearer abcd" }, "successResponses": { "statusCode": [ 200, 201, 202, 204 ] }, "unsuccessResponses": { "statusCode": [ 400, 403, 401, 404, 409, 501, 500 ] } } } |
Creating a Security System
The security system represents the connection between EIC and the target application. For more information on creating a security system, see Creating a Security System.
Creating an Endpoint for the Security System
Endpoint refers to the target application used to provision accounts and entitlements (access). For more information on creating an endpoint, see Creating Endpoints..
Using the ForgeRock - CIAM Integration
You can use the ForgeRock - CIAM integration for performing import and provisioning operations after configuring it to meet your requirements.
Guidelines for Using the Integration
You must apply the following guidelines for configuring import:
- Run account import before running the access import.
- Map all ForgeRock - CIAM attributes to EIC account attributes using ImportAccountEntJSON.
- Use Java ternary operators if you want to add conditions in the provisioning parameters. You can use Java operations to tweak any attributes by using if-else conditions, substrings, or operators in the JSON for provisioning.
Configuring Import Operations
- Full account import: When configuring the connection for the first time, first perform full import to import all existing accounts from the target application to EIC. To perform full import, the invoke API gets response from the target application and maps the attributes in the target application with attributes in EIC. As part of this process, the deleted accounts are also identified and marked as suspended from import service.
- Full Access import: When configuring the connection for the first time, first perform full import to import all existing access from the target application to EIC. To perform full import, the invoke API gets response from the target application and maps the attributes in the target application with attributes in EIC. As part of this process, the deleted entitlements are also identified and marked as inactive.
The import jobs are automatically created in EIC after you create a connection for the ForgeRock - CIAM integration. For more information about creating jobs, see Data Jobs.
Importing Accounts
You must import accounts after the users are available in EIC.
To import accounts:
- Specify the connection and import parameters. For more information, see Account and Access import.
Note: Ensure that the connection type is selected as REST. - Configure the Application Data Import (Single Threaded) / Application Data Import (Multi-Threaded) job to import accounts and access. For more information, see Data Jobs.
Configuring Provisioning and Deprovisioning
Provisioning is automatically enabled when a connection is configured. For detailed information about performing provisioning tasks, see Access Request System.
To provision objects to the target application:
- Specify the connection and provisioning parameters. For more information, see Configuration Parameters for Provisioning.
Note: Ensure that the connection type is selected as REST. - Configure the Provisioning job (WSRETRY). For more information, see Provisioning Jobs.
When a provisioning job is triggered, it creates provisioning tasks in EIC. When these tasks are completed, the provisioning action is performed on the target application through the connector.
Troubleshooting
To troubleshoot common problems with connectors, answer frequently asked questions, and provide solutions to a few common issues you might encounter while configuring or working with connectors, see Common Troubleshooting Guide for Connectors.
To troubleshoot common problems or obtain answers for frequently asked questions for REST connectors, see the REST Connector Guide.
