- Saviynt Forums
- Best Practice
- IGA Implementation
- Connector
- Active Directory best practice
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Notify a Moderator
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Notify a Moderator
on 07/10/2023 08:57 AM
Short Description
AD is one of the most commonly used connector. This article provides best practices for configuring AD connector
Applicable version
All versions
Detail best practice
- Try to use ObjectGUID as reconciliation Attribute in Account_Attribute parameter
Sample JSON for the Accounts Import -
[ACCOUNTID::objectGUID#String,
NAME::sAMAccountName#String,
DISPLAYNAME::name#String,
CUSTOMPROPERTY26::objectGUID#Binary,
RECONCILATION_FIELD::CUSTOMPROPERTY26]
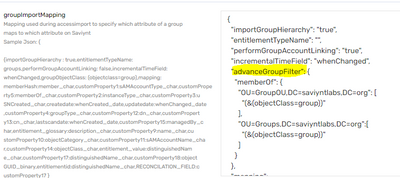
- Similarly map ObjectGUID as reconciliation Attribute in in groupImportMapping
Sample JSON for Group Import -
{
"entitlementTypeName": "",
"performGroupAccountLinking": "true",
"importnestedmembershipoutofscope": "true",
"incrementalTimeField": "whenChanged",
"groupObjectClass": "(objectclass=group)",
"mapping":"memberHash:member_char,customProperty1:sAMAccountType_char,customProperty2:instanceType_char,customProperty3:uSNCreated_char,customProperty4:groupType_char,customProperty5:dSCorePropagationData_char,customProperty12:dn_char,customProperty13:cn_char,lastscandate:whenCreated_date,customProperty15:managedBy_char,entitlement_glossary:description_char,description:description_char,displayname:name_char,customProperty9:name_char,customProperty10:objectCategory_char,customProperty11:sAMAccountName_char,entitlement_value:distinguishedName_char,entitlementid:distinguishedName_char,customProperty14:objectClass_char,updatedate:whenChanged_date,customPropErty17:distinguishedName_char,RECONCILATION_FIELD:customProperty18,customProperty18:objectGUID_Binary,
"tableFieldAttribute": "accountID"
}
- Implement AD Account incremental import with daily frequency. We need to add below attributes in Accounts Import mapping of AD Connector to enable the incremental Import and run the Incremental Import
CREATED_ON::whenCreated#date,UPDATEDATE::whenChanged#date
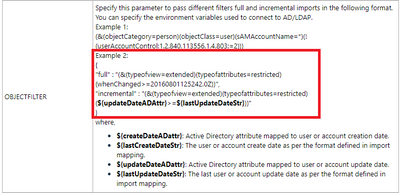
- AD User Incremental Import can be configured at the object filter level in AD Connector. Please find the object filter details in the below screenshot
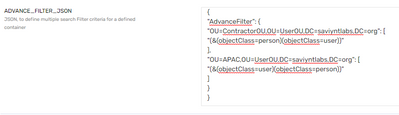
- Use ADVANCE_FILTER_JSON if you just want to import accounts from specific containers :
- Similarly, Advanced Group filter can be used in Group Import Mapping JSON to import groups from specific containers
- Schedule either AD accounts import or access import, don’t implement both. Both accounts and access triggers can bring Accounts and entitlements with the difference being Access imports also bring entitlements which are not yet assigned to any account
- If there are multiple AD domains then instead of multiple AD connectors per domain, make use of ADSI connector. Note - no need to use ADSI connector if there is only AD domain
- Ensure AD connection’s Status and threshold parameter has all the AD userAccessControl which can mark accounts’ status as Active or Inactive
Below are the possible Active status of AD userAccessControl. There might be some ddditional once specific to your customer so recommended to do a LDAP search before finalizing the status list
"activeStatus":["512","590336","2163200","640","66048","66080","544","262656","328192","328224","262688","2080","2097664"] - Make use of character "?" for null check. Example: "manager":"${managerAccount?.accountID}“
- Make sure REUSEINACTIVEACCOUNT parameter is marked FALSE. If this config is set to TRUE then the connector will reuse the existing inactive account name while creating new accounts. By default this will be set to TRUE so our recommendation is to set this value to false.
- SUPPORTEMPTYSTRING should be FALSE, in case you want to skip the null/empty values for any attribute during creation
Key Benefit
Better performance and ease of maintenance
Reference documentation
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Notify a Moderator
Hi @Rishi i am onboarding an LDAP application to manage group lifecycle and group access provisioning/reconciliation. Assuming it will follow the similar kind of setup as "AD". i have few questions/doubts here if you can look into and respond
1) In the provisioning job execution i see this line in logs "You must have objectGUID or objectSID present in ACCOUNT_ATTRIBUTE as a Reconcilation_Field".
objectGUID or objectSID is not present in LDAP but we have entryUUID which is unique for all LDAP accounts. Is it ok to use this attribute or its mandatory to have one of them (objectGUID or objectSID).
2) while provisioning users access to a ldap group i am getting this exception in logs
"java.lang.NullPointerException: Cannot invoke method toUpperCase() on null object"
what could be the issue here? Few of the log lines printed in given sequence from bottom to top
| Exception |
| java.lang.NullPointerException: Cannot invoke method toUpperCase() on null object at com.saviynt.ldap.SaviyntGroovyLdapService$_printBindingMap_closure43.doCall(SaviyntGroovyLdapService.groovy:5213) at com.saviynt.ldap.SaviyntGroovyLdapService.printBindingMap(SaviyntGroovyLdapService.groovy:5207) at com.saviynt.ldap.SaviyntGroovyLdapService$_provisionAccessToAccountGLDAP_closure4.doCall(SaviyntGroovyLdapService.groovy:1329) at com.saviynt.ldap.SaviyntGroovyLdapService.provisionAccessToAccountGLDAP(SaviyntGroovyLdapService.groovy:1242) at com.saviynt.ecm.services.ArsTaskService.provisionAccessToAccounttarget(ArsTaskService.groovy:11452) at com.saviynt.ecm.services.ArsTaskHelperService$_whenTaskTypeIsOneAddAccess_closure45.doCall(ArsTaskHelperService.groovy:2794) at com.saviynt.ecm.services.ArsTaskHelperService.whenTaskTypeIsOneAddAccess(ArsTaskHelperService.groovy:2785) at com.saviynt.ecm.services.ArsTaskHelperService$_completeAutoProvTasksUpgraded_closure1.doCall(ArsTaskHelperService.groovy:165) at com.saviynt.ecm.services.ArsTaskHelperService.completeAutoProvTasksUpgraded(ArsTaskHelperService.groovy:160) at MultipleProvisioningJob.execute(MultipleProvisioningJob.groovy:222) at org.quartz.core.JobRunShell.run(JobRunShell.java:199) at org.quartz.simpl.SimpleThreadPool$WorkerThread.run(SimpleThreadPool.java:546) |
| Inside getAttrUsingGUIDorSID method |
| Enter getLDAPContext |
| calling executeRequestWithTimeoutConfig for api... |
| calling api... |
| Enter acquireLDAPContext |
| Setting default timeout |
| Env Properties in IMPORTJSON: null |
| enable_dclocator = false |
| Exit getLDAPContext |
| called api... |
| timeout validated for api... |
| got response for api... |
| You must have objectGUID or objectSID present in ACCOUNT_ATTRIBUTE as a Reconcilation_Field |
| Result size= 0 |
| Query to update Account DN Attr: Select accountID from ACCOUNTS WHERE ACCOUNTKEY={userkey} |
| Enter getAssignedGroups |
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Notify a Moderator
@Rishi can we some writeup for AD service Account Management?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Notify a Moderator
@Manu269 sure, we will publish an article on service Account Management
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Notify a Moderator
can we know the incremental config for user import. The above config is not working for user import
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Notify a Moderator
Hi @trivi just use the CREATEDATE and UPDATEDATE configuration in USER_ATTRIBUTE configuration. that's it.