- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Privileged Access Management
- CPAM JIT Access permission segregation based on en...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CPAM JIT Access permission segregation based on entitlement
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/17/2023 04:17 AM
We have a scenario where set of users required admin access and other set of users not required admin access through JIT for the same AWS Linux Instances.
Is there a solution where we can achieve this use case to provide the admin access to set of users based on entitlement to the AWS linux instances where other set users not required a admin access using JIT to the same linux instances.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/17/2023 08:12 AM
@RMJ Thanks for posting your question. Yes, there is a way to do this. Please find below an example which check if user has a particular entitlement in GCP and assigns non-admin/admin permissions according to the entitlement user has. You can update the query to fit your requirement.
{"unix":{"command":"if [[ "${queryParam?.get(0)?.entitlement_value}" == *"view"* ]];then sudo useradd -m -s /bin/bash ${accountName} ;else sudo useradd -m -s /bin/bash ${accountName} -g google-sudoers;fi","queryParam": "SELECT IFNULL((select distinct ev3.entitlement_value from users u inner join arstasks arst on u.USERKEY=arst.USERKEY inner join endpoints ep on arst.endpoint=ep.endpointkey inner join entitlement_values ev on ev.ENTITLEMENTID=ep.CUSTOMPROPERTY17 Inner Join entitlement_types et on ev.entitlementtypekey = et.entitlementtypekey and et.Entitlementname = 'Project' inner join entitlement_values ev1 on ev.ENTITLEMENT_VALUE=SUBSTRING_INDEX(ev1.ENTITLEMENT_VALUE,'~',1) inner join entitlement_types et1 on ev1.entitlementtypekey=et1.entitlementtypekey and et1.Entitlementname = 'Project_Roles' inner join entitlement_values ev2 on ev2.ENTITLEMENT_VALUE=SUBSTRING_INDEX(ev1.ENTITLEMENT_VALUE,'~',-1) inner join entitlement_types et2 on ev2.entitlementtypekey=et2.entitlementtypekey and et2.Entitlementname = 'Role' inner join entitlements2 e2 on e2.ENTITLEMENT_VALUE1KEY=ev2.ENTITLEMENT_VALUEKEY inner join entitlement_values ev3 on e2.ENTITLEMENT_VALUE2KEY=ev3.ENTITLEMENT_VALUEKEY inner join entitlement_types et3 on ev3.entitlementtypekey=et3.entitlementtypekey and et3.Entitlementname = 'RolePermission' and ev3.ENTITLEMENT_VALUE in ('compute.instances.osAdminLogin') inner join user_accounts ua on arst.userkey=ua.userkey inner join accounts ac on ac.ACCOUNTKEY=ua.ACCOUNTKEY inner join account_entitlements1 ae1 on ae1.ACCOUNTKEY=ac.ACCOUNTKEY inner join entitlement_values ev4 on ev4.entitlement_valuekey=ae1.entitlement_valuekey Inner Join entitlement_types et4 on ev4.entitlementtypekey = et4.entitlementtypekey and et4.Entitlementname = 'Project_Roles' and ev4.ENTITLEMENT_VALUEKEY=ev1.ENTITLEMENT_VALUEKEY and arst.tasktype=3 and arst.STATUS=1 and u.username='${user.username}' and arst.TASKKEY=${tasks.id} limit 1), 'view') as 'entitlement_value'"}}
Thanks
Nagesh K
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/19/2023 12:19 PM
Hi Nagesh,
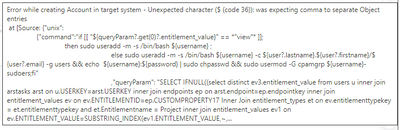
We tried to use below provision command, but it is failing with following error while launching session.
Error Message: 'Error while creating Account'
Command:
{"unix":{"command":"if [[ "${queryParam?.get(0)?.entitlement_value}" == *"view"* ]];then sudo useradd -m -s /bin/bash ${username};else sudo useradd -m -s /bin/bash '${username}' -c '${user?.lastname}.${user?.firstname}/${user?.email}' -g users && echo ${username}:${password} | sudo chpasswd && sudo usermod -G cpamgrp ${username}-sudoers;fi","queryParam": "SELECT IFNULL((select tbl.entitlement_value from (select 'CPAM_PlatformAdmins' entitlement_value from dual) tbl), 'view') as 'entitlement_value'"}}
Regards,
Shravan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/24/2023 11:15 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/25/2023 06:23 AM
@Shravan The error you are seeing is due to the double quotes not being escaped. I referred to the documentation and it was indeed escaped rightly there. Earlier versions of the product allowed the query to run without escaping but the later versions need it.
Also, the task type and status values should be changed as we are not creating a "new account" task anymore when we submit JIT request. I'm following up internally on this and will get back. In the meanwhile can you try the below option and see if that works?
1. Navigate to Global Config -> select Tasks in the left dropdown and in the text field for "Instant Provisioning Tasks" remove the option Emergency Access Instance Grant Access
2. In the above query, add the escape for quotes as given in the second sample query in this article : Configuring Quick Access. And change the tasktype and status conditions as below
and arst.tasktype=34 and arst.STATUS=3
3. Also the above query is an example for checking if user has a specific GCP project role. Is that what you are trying to check in your environment? If not, you should modify the query accordingly
4. Now submit the JIT request, let the Enterprise Role job run and create a task. Then run wsretry and see if the provisioning works fine.
Thanks,
Nagesh K
- Disconnected application selected data loading format for Child Entitlement in Identity Governance & Administration
- If condition in acctEntMappings for setting entitlement_value in Identity Governance & Administration
- Enterprise Role Association to 17K Users Recommendation in Identity Governance & Administration
- Need Help: SAP Role Description Not Showing in SOD Evaluation via API in Application Access Governance
- EntitlementValueImportJob got failed in Identity Governance & Administration
