- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- Re: LDAP Group Provisioning - Failure - isMemberO...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/30/2022 12:06 PM
Hi All,
We are connected to OUD and where group assignment is based on isMemberOf (Account Level) and UniqueMember(Group level) attributes.
We reconciled all LDAP groups to Saviynt on entitlement type isMemberOf, when we are trying to provision group access, it fails. provisioning comment is given below.
Error while ADD operation for account-smurfaccount to Group-cn=ABC,ou=Groups,dc=xyzcompany,dc=com in AD - [LDAP: error code 65 - Entry uid=smurfaccount,ou=people,dc=xyzcompany,dc=com cannot not be modified because the resulting entry would have violated the server schema: Entry uid=smurfaccount,ou=people,dc=xyzcompany,dc=com violates the Directory Server schema configuration because it includes attribute which is not allowed by any of the objectclasses defined in that entry]
does the connector lookup only for member attribute by default or it checks uniqueMember too for access assignment ?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/30/2022 02:37 PM
Hi Sudhakar,
The missing configurations can cause this error and these are required for addition/removal of access on LDAP targets. please try below steps and see if it helps in resolving your issue.
Steps for Solution:
1) Validate Connection Configuration at the Endpoint
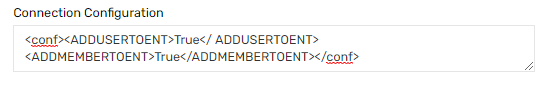
The connection configuration attribute at the endpoint must have the following configuration setup.
<conf><ADDUSERTOENT>True</ ADDUSERTOENT> <ADDMEMBERTOENT>True</ADDMEMBERTOENT></conf>
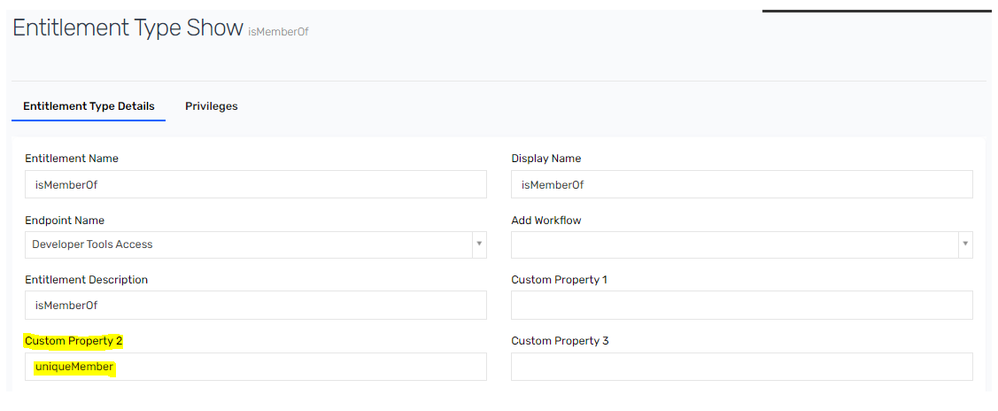
2. Validate customproperty2 of the entitlement type
The customproperty2 of the entitlement type must be set to the attribute which holds the membership in the LDAP target system in the groups. For example – in Active Directory, groups store the membership in the member attribute of the groups, similarly Open-DJ Directory groups stores the membership in the uniqueMember attribute.
Thanks & Kind Regards,
Manikanta.S
Manikanta.S
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
06/02/2022 03:00 AM
Thanks Manikanta, It worked
- Enterprise Role Association to 17K Users Recommendation in Identity Governance & Administration
- Child and Parent group assignment is not happening while creating the Entra ID Group from Saviynt in Identity Governance & Administration
- Add access for Netsuite application failed. in Identity Governance & Administration
- Instruction to provisioning team for new account tasks generated thorough BR in Identity Governance & Administration
- Store entitlements in account request in Identity Governance & Administration