- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- Entitlements with new account feature is trying to...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 08:22 AM
We are using the functionality "Entitlements with New Account" on one of our endpoints to place the user into an Active Directory group entitlement when a new account is requested for that endpoint. All users already receive AD accounts with birthright and accounts can only be requested for this endpoint through ARS. Unfortunately, it is not working as expected. We are seeing that the request creates an add access task for the AD entitlement but then the task itself appears to actually be trying to CREATE an Active Directory account itself. Of course, this fails, because the user already has an AD account and it cannot pass the unique value constraint at creation time. Has anyone seen this and can advise maybe what's happening?
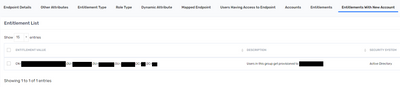
Endpoint config:
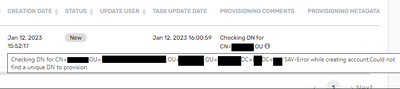
The task and error that gets generated by this. You can see it is an Add Access task but in the provisioning comments it's doing a check for unique to create the account instead:
Complete error:
Solved! Go to Solution.
- Labels:
-
Defect or Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 11:38 AM
Does your existing account correlated with user ?
Did you enabled entitlementsonly under security system for create task action option
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 12:51 PM
Good questions. Yes, the account is correlated. I have seen that consistently across every time we've had this problem.
Create Task Action option is blank/empty for both of the security systems involved with this issue. What is the behavior of that setting?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 01:46 PM
Do have below setting ON/OFF on AD endpoint?
Disable New Account Request if Account Already Exists
If it is OFF can you make it ON and see how it behaves?
If you have use case where user will have multiple AD accounts under one endpoint then you cannot make above suggested change. But I just want to give it a try to see behaviour
Regards,
Saathvik
If this reply answered your question, please Accept As Solution and give Kudos to help others facing similar issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 01:52 PM
Under Active Directory endpoint, this is already set to ON.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 01:55 PM
Does account name from task suppose to be created vs newly created account is same ?
when user tries to request he see new account or modify account?
Do you have just 1 endpoint for ad correct
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 01:58 PM
Account name in the task matches their systemusername which is what we use to generate the AD account. They already have an AD account which is associated to their user record, and it is active. There should be no reason it would try to create a new AD account with this config, as far as I can tell. When they request to modify account they will see the existing account they have associated.
Only 1 endpoint for AD.
Also, I wanted to mention we have the same config in place for a different endpoint doing almost the exact same thing, but placing the user into a different AD group. And that one appears to work as expected! I cannot see any differences between the endpoints.
It feels like a bug but I have a support ticket open that is moving slowly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 02:06 PM
Systemusername of user should be used to create DN Of ad.
does dn of both accounts matching ?
what is accountid of current account ?
what is your createaccountjson
enable entitlementsonly under security system it should solve ur issue
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 02:42 PM
Systemusername of user should be used to create DN Of ad.
That is correct.
does dn of both accounts matching ?
The AD account that they already have and the one it is trying to create (which it should not be doing) have the same dn.
what is your createaccountjson
Not sure that this is relevant? It should not be running CreateAccountJSON. That is the issue. There should be no attempt to create an account for adding access.
enable entitlementsonly under security system it should solve ur issue
I'm not sure on this because on the other endpoint where this configuraton is working, it also does not have 'EntitlementsOnly' specified under the Create Tasks config. How could it work for that endpoint but not this one?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/20/2023 02:55 PM
Since its trying share create account json and enable config at security system legel
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/23/2023 07:42 AM
I thought of one difference between the endpoint where this config works and the endpoint where it causes this issue. The endpoint where it works does not have entitlement approval workflow for *most* entitlements. The endpoint where we have this issue has an approval for every single request. Is this where setting "EntitlementsOnly" for Create Task Action is beneficial for this scenario? It would instruct the endpoint to only create a task for the entitlement after it is approved?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
01/23/2023 07:46 AM
Yes
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
05/03/2023 05:37 AM
Turns out that this was a bug fixed in 2021. We were on version 2020.1. When we upgraded to 23.x the issue was resolved.
- Box OOTB Connector Operations in Identity Governance & Administration
- Active Directory Entitlement Import in Identity Governance & Administration
- Azure Entra ID Endpoint Filtering resulting in duplicate entitlements in Identity Governance & Administration
- Cleaning of duplicate entitlement types in salaeforce in Identity Governance & Administration
- Other entitlement details - Entitlement map in Identity Governance & Administration