- Saviynt Forums
- Enterprise Identity Cloud Discussions
- Identity Governance & Administration
- Re: Adding accounts to entitlement dynamically bas...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Adding accounts to entitlement dynamically based on another entitlement
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
11/29/2022 11:45 AM
Hello,
I am trying to check if there is a way to assign an entitlement to the user account based on another entitlement. For example, if a user has an entitlement with name containing a keyword(say aws) for the same endpoint then the user should automatically get Entitlement B.
One way is using the entitlement map and adding the entitlement to each entitlement having the aws keyword. But this not scalable as there will be hundreds of new entitlements created and each time we need to add the map for the newly created entitlement.
Other way is to use actionable analytics. But again this requires scheduling the analytics job and the requirement is that the addition of the automatic entitlement should be instant.
Can we trigger actionable analytics through some rule? Or Is there any other way to achieve this requirement?
- Labels:
-
Admin
-
Analytics
-
Provisioning
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
11/29/2022 01:41 PM
You can create request rule other 2 solutions you have already listed
entitlement map
actionable report
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
11/30/2022 06:48 AM
@rushikeshvartakCan you please elaborate? I am not able to understand which condition to use.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
11/30/2022 06:41 PM
Request Rule https://saviynt.freshdesk.com/support/solutions/articles/43000431687-creating-request-rules
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/02/2022 11:20 AM
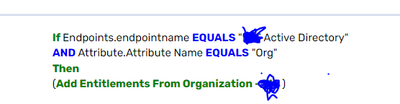
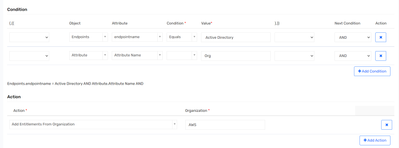
I followed the steps but the Request Rule is not getting triggered even after the approval process is completed. Below is the rule i created.
Also I don't see Rules tab in the Organization that i created.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/02/2022 01:09 PM
Did you ran wsretry
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/02/2022 01:59 PM
Yes. There is no error in the logs. The pending tasks from the actual request are also created and completed.
Assuming it works, This still does not meet the use case requirement. If I am asking the user to select a dynamic attribute from the form then how is it different from asking the user to select that particular entitlement itself from the requestable entitlement list. The requirement here is that all users selecting any other aws entitlement should not have to select the console entitlement or any other dynamic attribute.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/02/2022 03:07 PM
Whats issue with analytics report ?
please share request rule
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/02/2022 03:45 PM
The analytics report needs to be scheduled and client does not want the end user to wait for job as the user needs to login to aws console( with that entitlement) immediately after the account request approval. They have explicitly stated that the process should be automated and not job based.
Request rule -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/02/2022 05:09 PM - edited 12/02/2022 05:09 PM
Does endpoint name matching with name visible on request history?
analytics you can run before wsretry and end user doesn’t need to wait
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/04/2022 09:01 PM
Yes, the name is matching.
They don't want to be go with Analytics option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/04/2022 09:03 PM
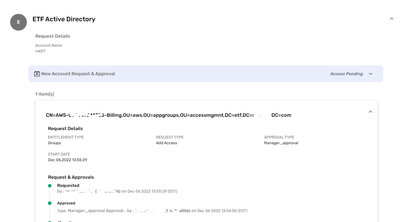
Share logs after wsretry run and ARS Request history screenshot
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/06/2022
11:13 AM
- last edited on
12/08/2022
08:03 AM
by
![]() Dave
Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/06/2022 07:42 PM
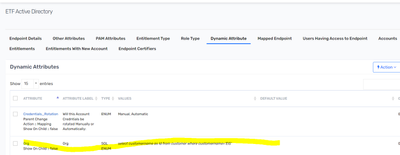
There is no attribute name with Org
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/06/2022 07:49 PM
Where? In the endpoint ?
It is there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/06/2022 07:58 PM
on Request Approval
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/07/2022 07:58 AM
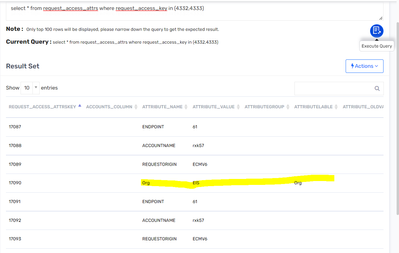
I don't know why it is not showing on UI. But it is there in the request_access_attrs table.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/07/2022 01:02 PM
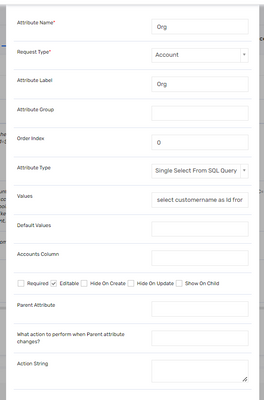
Share dynamic attribute config
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/07/2022 09:50 PM
SQL - select customername as Id from customer where customername='EIS'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/09/2022 10:12 AM
@rushikeshvartak did you find anything from the logs or screenshot? Is there any configuration which is missing or incorrectly done? Let me know. Based on the feedback I need to create ticket if its a defect or if the feature is not working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/09/2022 10:35 AM
Please store Dynamic attribute value in accounts column
Regards,
Rushikesh Vartak
If you find the response useful, kindly consider selecting Accept As Solution and clicking on the kudos button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/09/2022 11:08 AM
@rushikeshvartak Still after storing it as cp value in accounts column and after running the wsretry, the request rule task is not getting created.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify a Moderator
12/14/2022 07:31 AM
@rushikeshvartak Do you think any other config that I missed?
- Variations within Security Systems in Identity Governance & Administration
- ServiceNow plugin and default forms data filtering and form management in Identity Governance & Administration
- REST Connector - All Entitlements as input in Identity Governance & Administration
- the Endpoint access query needed to not show an app in ARS if the user belongs to XYZ Entitlement in Identity Governance & Administration
- Generate Entitlement displayname from entitlement_value on import job in Identity Governance & Administration